In this article, we discuss Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP). We define what they are, discuss the risks they pose to mobile devices and end users, go over some key characteristics, and then show you how the mobile app intelligence solutions we provide at 42matters can be used to detect them. With that, let’s cut to the chase.
Here’s what we cover in this blog post (click the links to jump to the corresponding section):
- What Are Potentially Unwanted Applications (PUA)?
- What Are Potentially Unwanted Programs (PUP)?
- Common Characteristics of Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP)
- The Dangers, Risks, and Consequences of Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP)
- How to Detect Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP)
- API Tools for Detecting Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP)
To learn how app intelligence can be used to detect and blacklist PUAs, chat with our team!
What Are Potentially Unwanted Applications (PUA)?
A Potentially Unwanted Application (PUA) is an app installed on a mobile device or computer that may put user security or privacy at risk or otherwise cause undue degradations in user experience. Classified as grayware, PUAs aren’t necessarily malicious by design. They may be created by legitimate or illegitimate software publishers and their impact may either be inadvertent or intentional.
Moreover, not all PUAs are destructive. Some merely cause very annoying behavior, like generating pop-up ads or causing devices to run slowly. Indeed, more often than not, apps are deemed PUAs because they unwittingly use clunky software development kits (SDKs), low-quality ad networks, or overly intrusive permissions.
What Are Potentially Unwanted Programs (PUP)?
Potentially Unwanted Programs (PUPs) impact users and devices in the same way. However, while PUAs refer to mobile apps installed onto clients by end users, PUPs typically refer to things like risky software and malicious SDKs that are bundled into apps by their developers.
Again, PUPs aren’t necessarily malicious in intent (they may just be annoying), but because they’re typically buried in app tech stacks, users are unlikely to know about them and will often unwittingly consent to letting them operate in the background of their devices.
Common Characteristics of Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP)
Digging a little deeper now, here are some of the most common PUA and PUP traits:
- User Consent Issues: The main issue with PUAs and PUPs is the lack of clear consent from the user. They might be installed through deceptive practices or hidden within the terms of a software installation.
- Bundled Software: Legitimate applications often integrate PUPs in their tech stacks, meaning users don’t necessarily know they’re using them and therefore don’t necessarily give informed consent.
- Adware and Toolbars: Many PUAs consist of adware or unnecessary toolbars. They can change browser settings, display excessive or unwanted advertisements, or redirect search queries to specific websites.
- Limited Functionality Programs: Some PUAs are programs that offer limited functionality or require a purchase to unlock all features. They might be marketed aggressively or deceptively to persuade users to buy the full version.
- Privacy Concerns: PUAs can pose privacy risks by collecting data on user behavior, browsing habits, or personal information without user consent.
- System Performance Impact: They can affect system performance by running unwanted processes in the background, consuming system resources, or causing stability issues.
- Security Risks: While not inherently malicious like malware, PUAs can pose security risks due to poor programming, vulnerabilities, or behaviors that weaken system security.
- Difficult to Remove: Since PUPs are typically installed onto apps by developers, there’s very little end users can do to mitigate the threat other than uninstall the app entirely.
The Dangers, Risks, and Consequences of Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP)
While Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP) aren’t typically as harmful as traditional malware, they nevertheless present end users and end user devices with a host of risks and possible consequences.
The most common risks associated with PUAs are…
- Privacy Intrusions
- Reduced System Performance
- Adware and Annoying Advertisements
- Browser Hijacking
- Security Vulnerabilities
- Bandwidth Consumption
- Deceptive Practices
- Legal and Compliance Risks
- Conflicts with Legitimate Software
Let’s take these one at a time…
Privacy Intrusions
Many PUAs and PUPs are designed to track user behavior, collect data, and transmit personal information. This can include browsing habits, search history, and even personal details, leading to privacy breaches.
Reduced System Performance
PUAs can consume system resources, leading to slower device performance, reduced response times, and an overall degradation in user experience. They often run in the background, utilizing CPU and memory resources.
Adware and Annoying Advertisements
A common type of PUA is adware, which floods users with unwanted advertisements. These ads can be intrusive, appearing as pop-ups or banners, and can sometimes redirect users to malicious sites.
Browser Hijacking
Some PUAs take control of web browsers, changing settings like the homepage or search engine without user consent. This can lead to unwanted redirects, exposure to more ads, and difficulty in restoring original settings.
Security Vulnerabilities
While not directly malicious, PUAs can create security holes in a system. They might weaken firewall settings or interfere with security software, leaving the system more vulnerable to serious malware attacks.
Bandwidth Consumption
These applications can consume internet bandwidth, either by displaying ads or by downloading additional unwanted software, which can be particularly problematic for users with limited data plans.
Deceptive Practices
Some PUAs and PUPs are disguised as legitimate software, tricking users into downloading them. They might claim to offer beneficial services but instead provide little to no value.
Legal and Compliance Risks
In a business environment, PUAs and PUPs can lead to compliance issues, especially if they collect and transmit data without proper authorization, potentially violating privacy laws and regulations.
Conflicts with Legitimate Software
PUAs can interfere with the normal operation of legitimate software, causing conflicts, errors, or crashes, which can be particularly disruptive in a work environment.
How to Detect Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP)
Alright, now that we’re clear on the basics, let’s turn our attention to how you can actually detect PUAs and PUPs in the mobile app and SDK market. Unfortunately, there are very few silver bullets and catch-alls here, and dead giveaways are few and far between. Instead, you’ll need to learn to spot the red flags so you can investigate apps further or preemptively blacklist them. You’ll also need the ability to audit these apps regularly so you can stay apprised of any noteworthy changes or updates.
To do this, many organizations use solutions like our suite of app intelligence APIs and file dumps, which provide programmatic access to app data from 20M+ apps across 12 leading mobile and connected TV (CTV) app stores. However, you can also use the 42matters Explorer, our flagship app market research platform. And since it has a visual and user-friendly dashboard, we’ll use it to demonstrate some critical PUA/PUP detection techniques.
Here’s what it looks like when you fire it up:
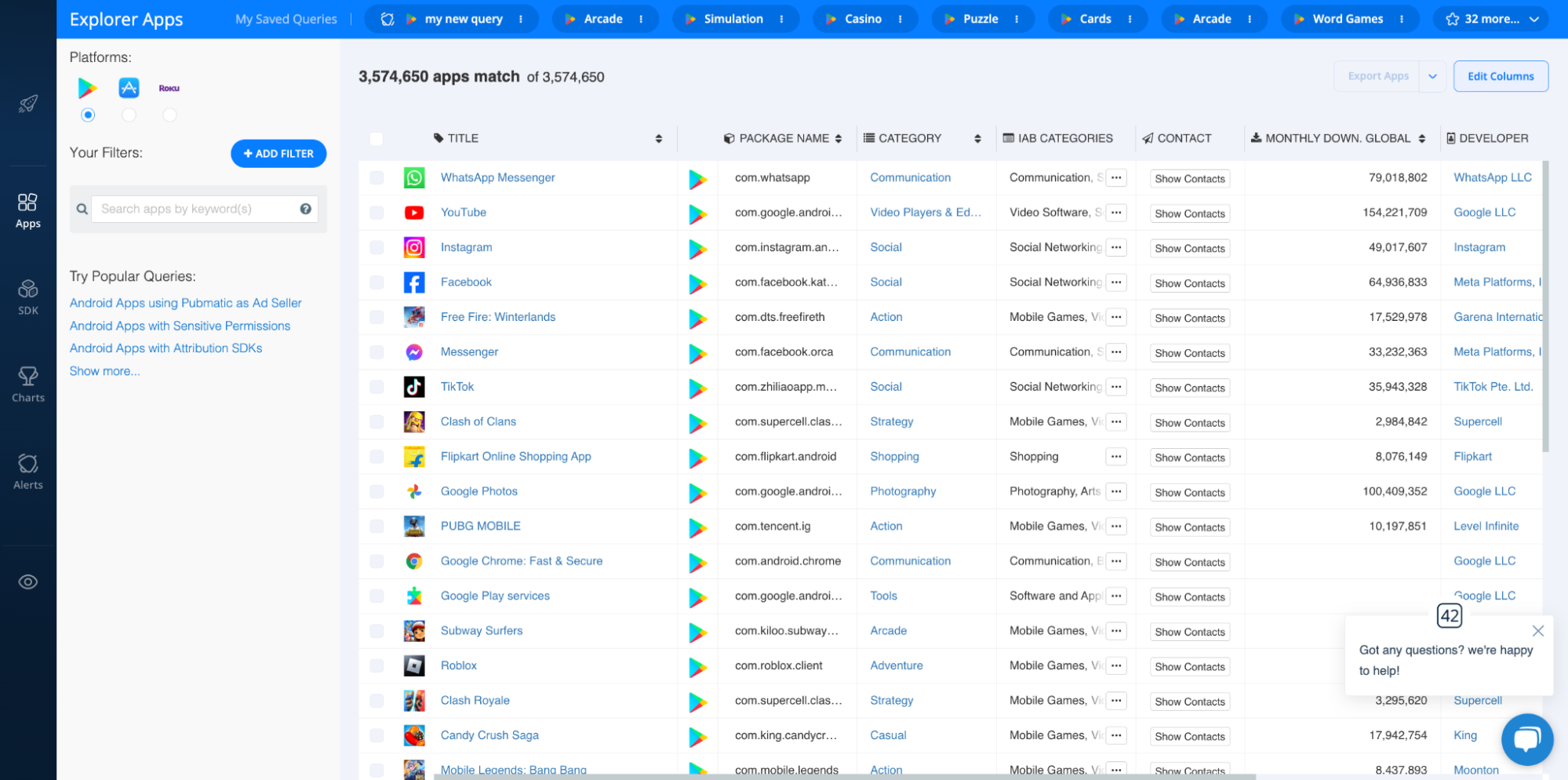
With this dashboard, you can browse millions of apps, games, and publishers, and access a variety of helpful insights and analytics to power your business.
While the Explorer provides a ton of mobile and CTV app intelligence, let’s maintain our focus on detecting PUAs and PUPs. You can use the 42matters Explorer to spot 14 common red flags for identifying PUAs and PUPs:
- Sensitive Permissions
- Location Tracking
- Privacy Policy
- Reviews and Review Sentiment
- Publisher and Publisher Website
- Required Capabilities
- Update Frequency and Abandoned Apps
- Publication Status
- Advertisements and app-ads.txt
- Integrated SDKs
- Registration Country
- Age Rating and Parental Advisories
- App ID, ID, and Bundle ID
- Downloads, Monthly Active Users, Other Performance Metrics
Let’s go over these one at a time!
Sensitive Permissions
First and foremost, permissions. Permissions serve as a method for managing and restricting access to certain functions at the system and device level for software. Generally, these permissions encompass capabilities that could impact privacy, including the potential to interact with a device's hardware features and personal data.
One of the biggest red flags when it comes to identifying grayware is if an app requests permission for things that seem unnecessary for its functionality. For example, if a simple gaming app asks users for access to contacts or messages, this should arouse your suspicion immediately.
With the 42matters Explorer, you can identify all apps that use undesirable permissions. This can be done two ways. First, by applying the PERMISSIONS filter:
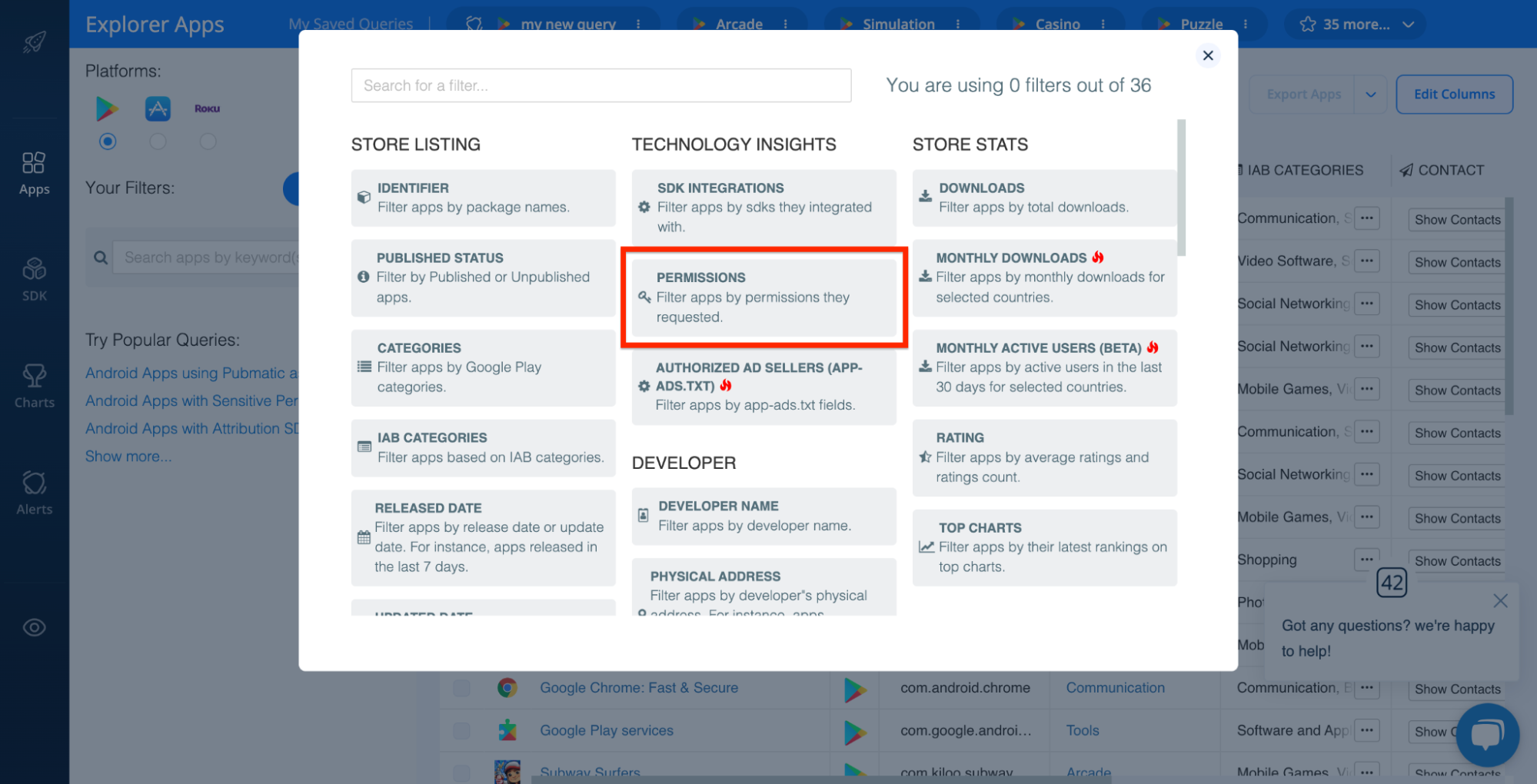
This filter makes it especially easy to zoom in on riskier permissions since it tags them with the orange ‘Sensitive permission’ label:
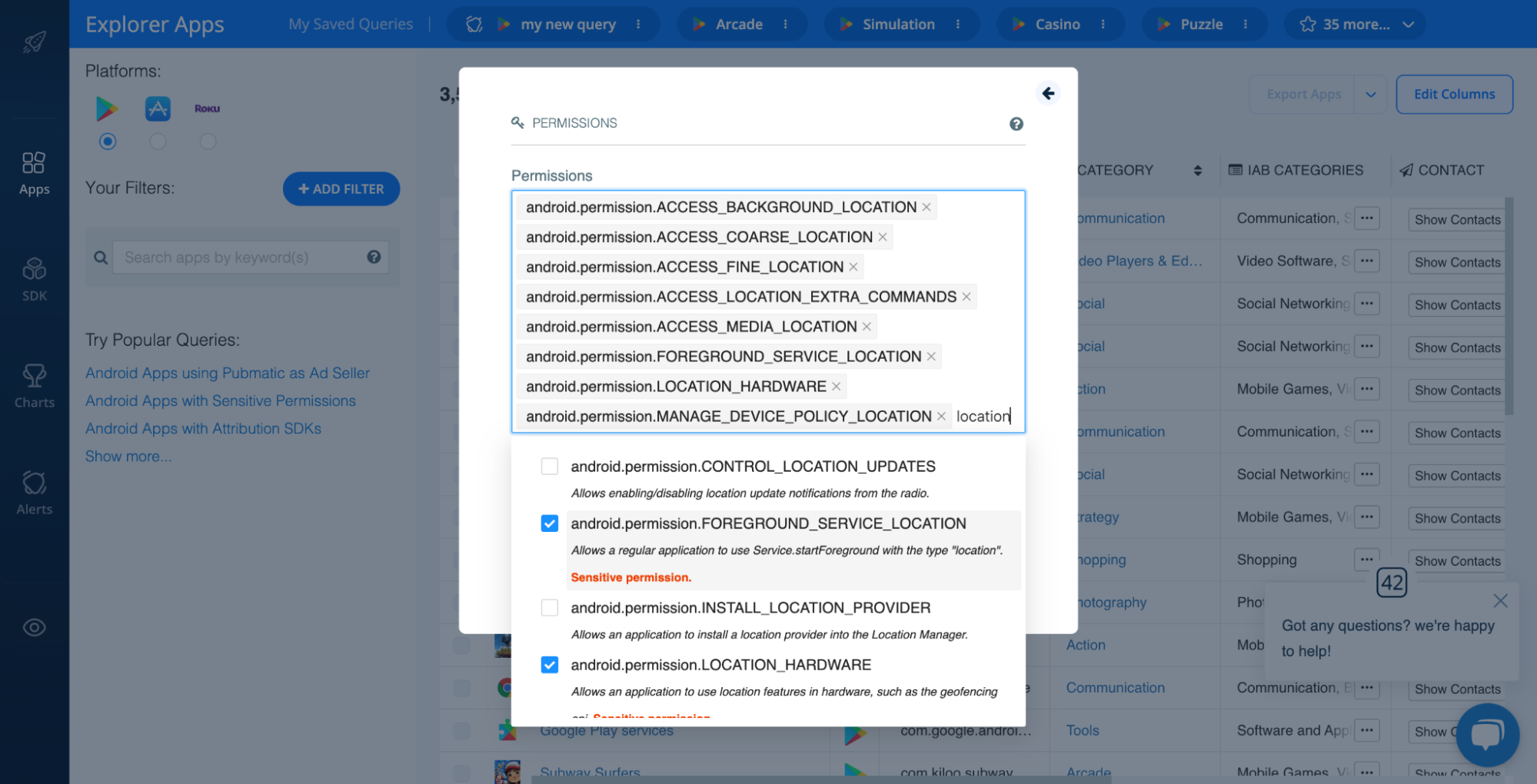
Once you apply this filter, you’ll see all apps that use the permissions you selected. In this case, these are all published Android apps that use any location permissions marked as sensitive:
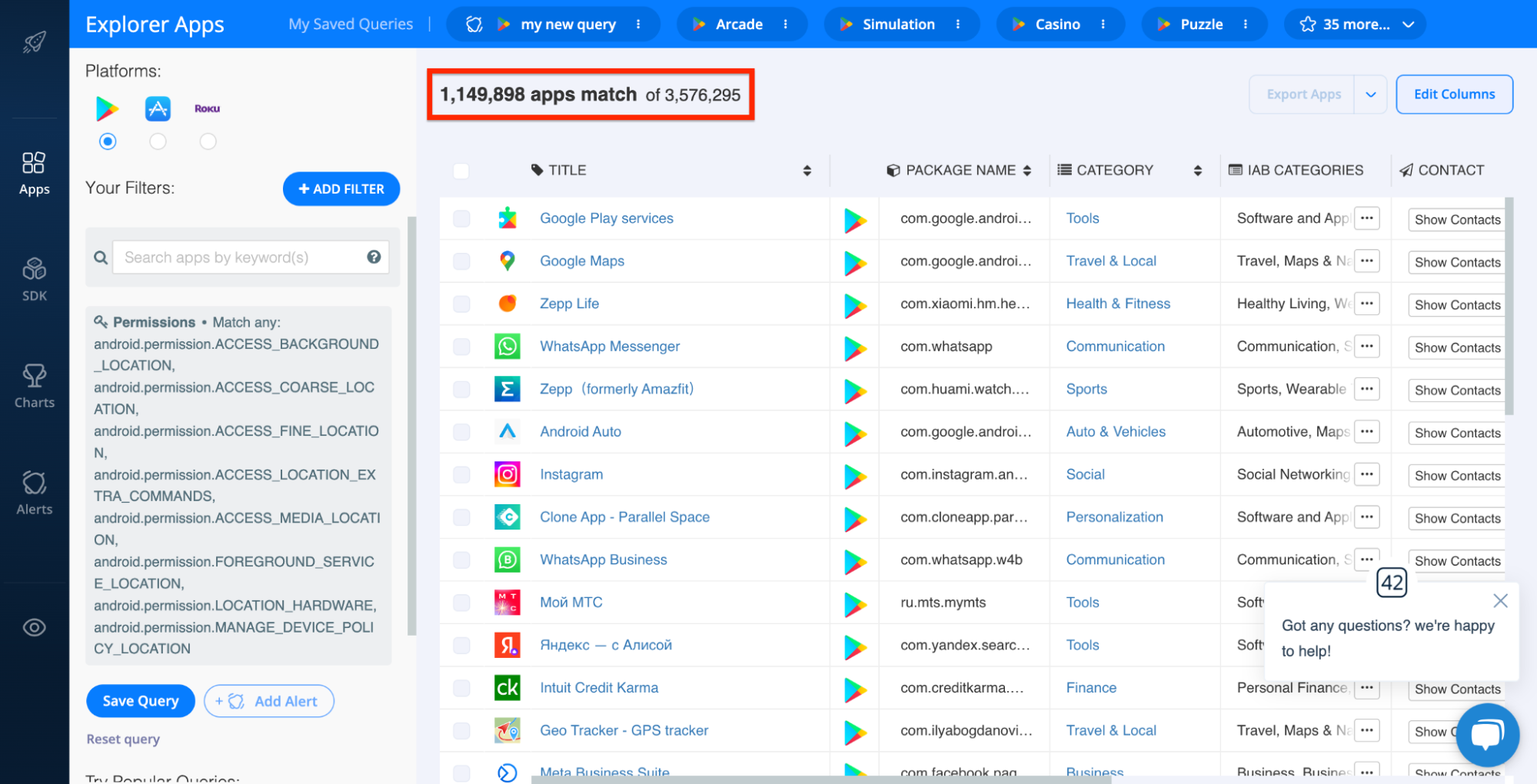
The second way to identify apps with risky permissions is by auditing specific apps. To do this, find the app you’d like to analyze in the Explorer, open its app profile, and scroll to the PERMISSIONS section. Here’s what this looks like for the Android version of WhatsApp:
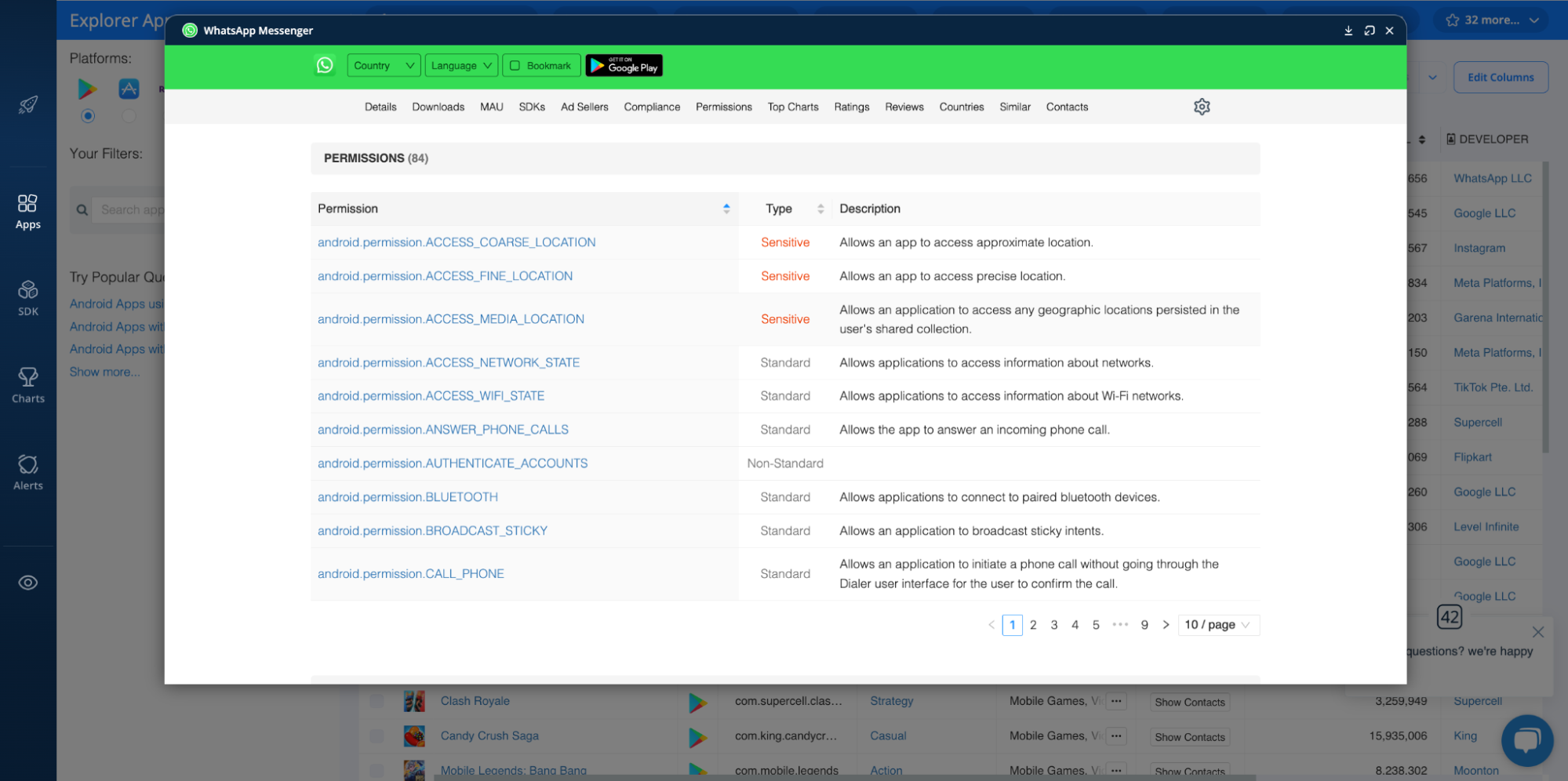
As above, riskier permissions are marked with the orange ‘Sensitive’ tag.
One thing to note before we move on. Apps that use sensitive permissions are not necessarily engaged in malicious activity. In fact, the vast majority of apps that do require them to function properly. That said, in environments where mobile app security is of the utmost importance — such as enterprise organizations or government agencies — it’s better to be safe than sorry.
Location Tracking
These days, location tracking is pretty widespread. Based on our data, for instance, there are 860k+ iOS apps and 1.15M+ Android apps that include sensitive location-related permissions.
However, this doesn’t mean there are 2M+ apps looking to exploit users via their location data. It means there are 2M+ apps that require closer scrutiny. Indeed, apps that appear to unnecessarily track location could be intrusive, signaling potential privacy concerns.
To find apps that use location tracking, follow the steps outlined above in the ‘Sensitive Permissions’ section above. Home in on all location-related permissions, like ACCESS_BACKGROUND_LOCATION, ACCESS_COARSE_LOCATION, ACCESS_FINE_LOCATION, etc.
Privacy Policy
Next up, it’s important to scrutinize app privacy policies. Of course, the first check is to make sure that an app actually has one in place. If it doesn’t, this should immediately call into question the app’s legitimacy. While it’s possible the publisher simply hasn’t gotten around to publishing its policy, most legit publishers are pretty good about doing so.
With the Explorer, you can use the Privacy Policy filter to block apps without policies:
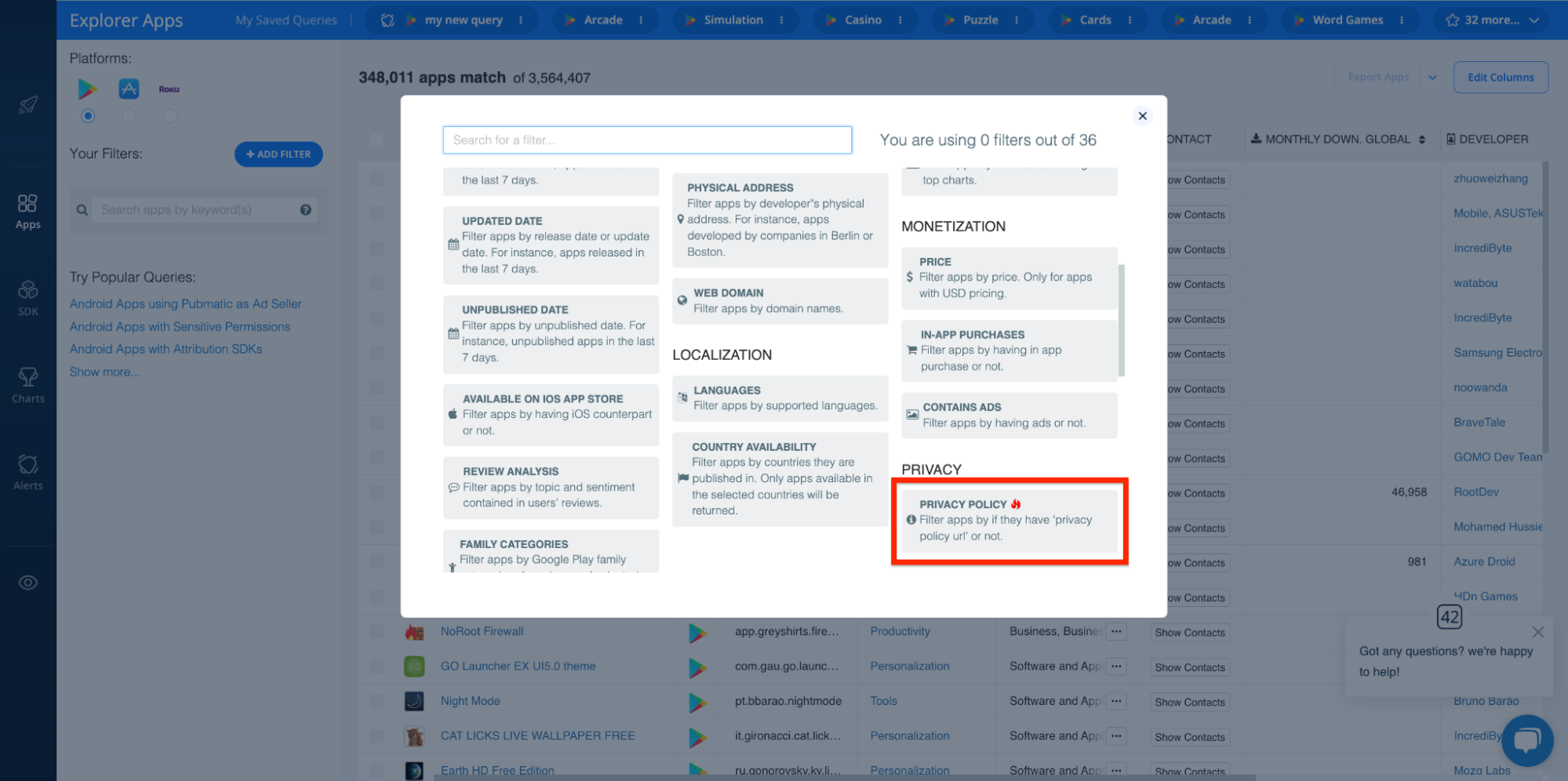

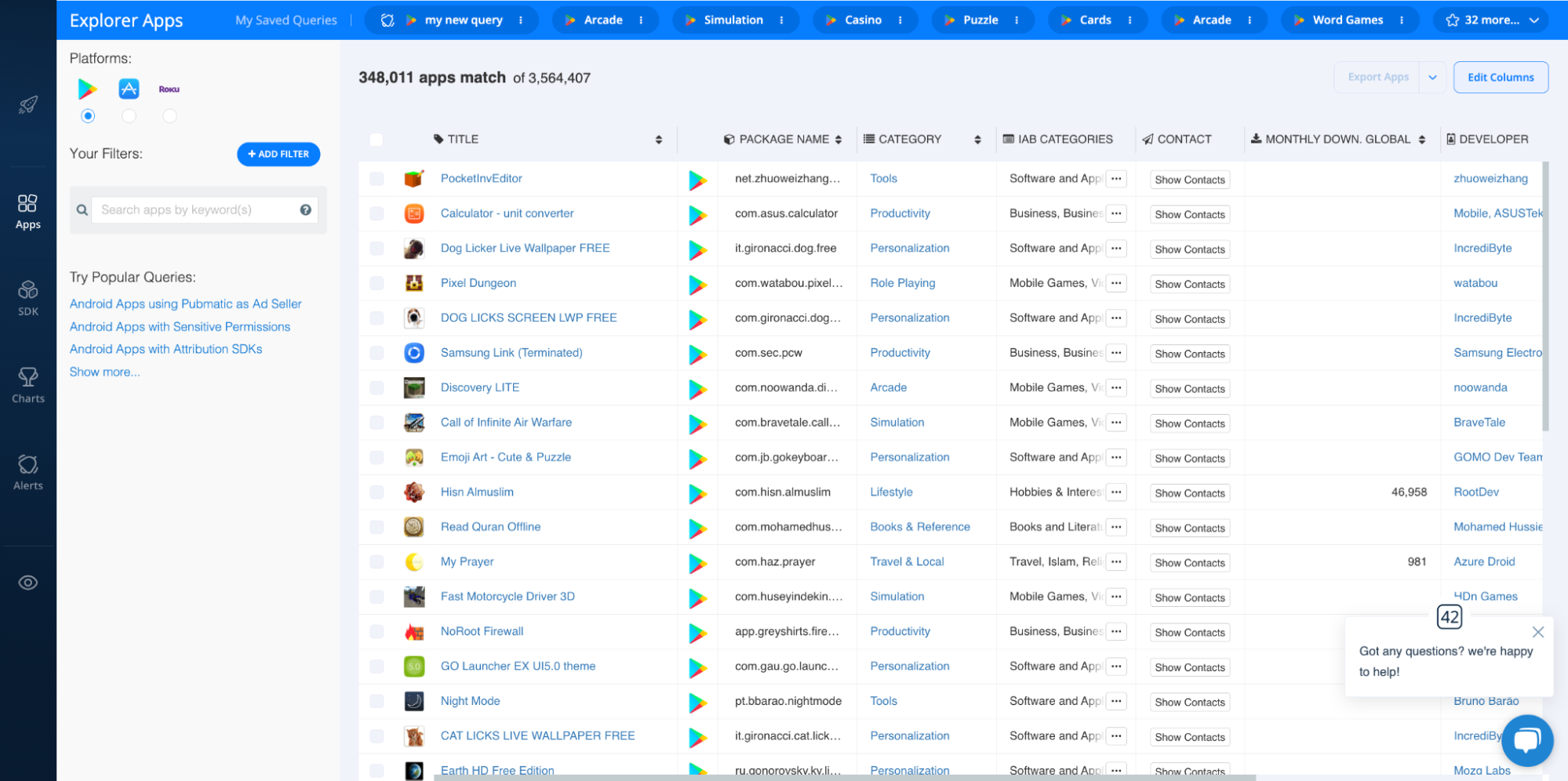
That said, even if a publisher has released a privacy policy, it’s worth giving it a quick read. Vague or sloppy policies are a major indicator that the publisher may not take user privacy seriously. It’s important to understand how an app will use and protect user data and whether the app complies with privacy regulations like GDPR, CCPA, COPPA, etc.
With the 42matters Explorer, you have easy access to app privacy policies. Simply click on an app of interest and click on the privacy policy link. Check it out:
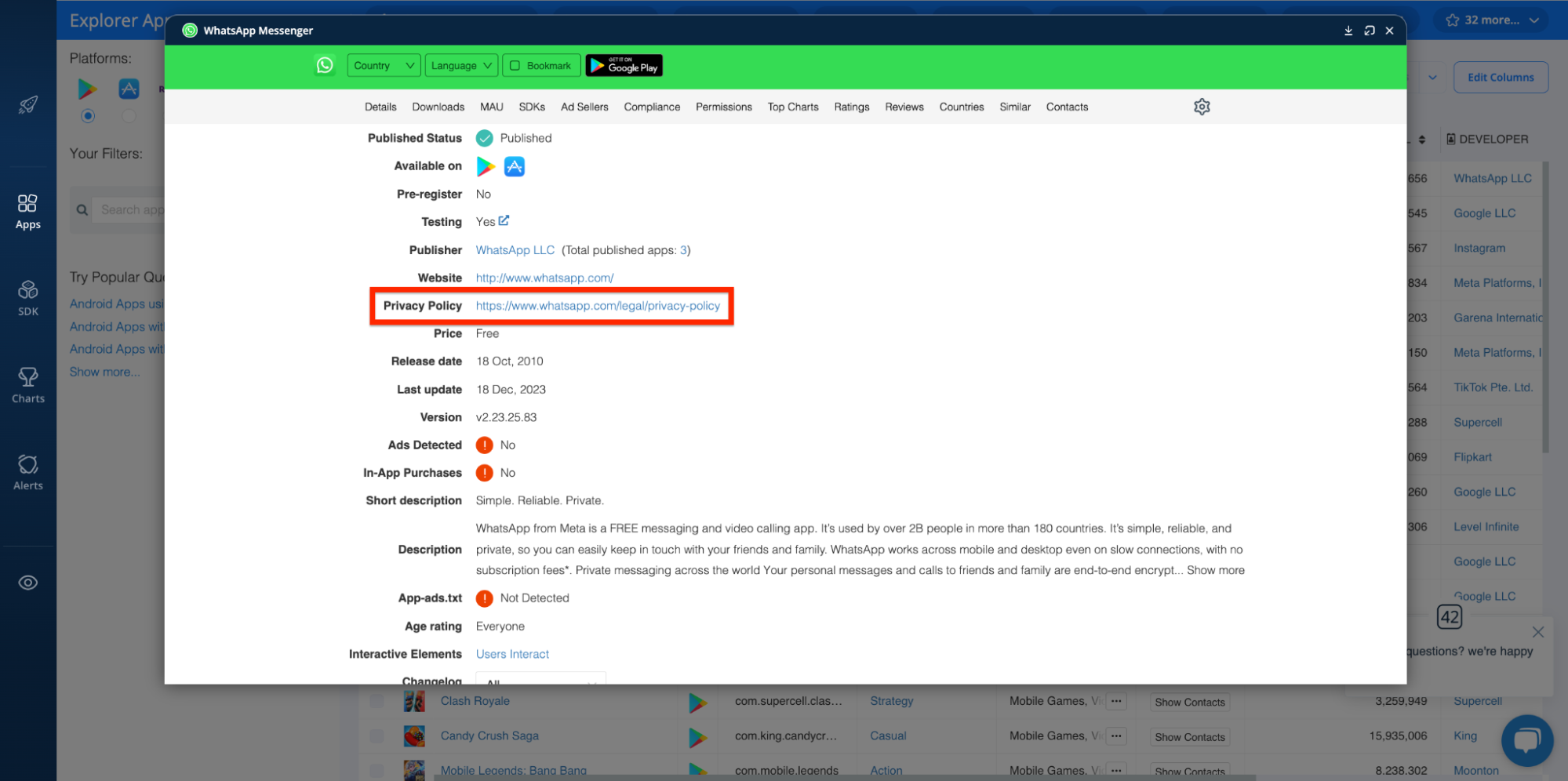
Reviews and Review Sentiment
Perusing negative reviews or reviews indicating unwanted behaviors (like excessive ads or privacy concerns) is another way to spot PUAs/PUPs.
The 42matters Explorer provides a quick glance at review sentiment:
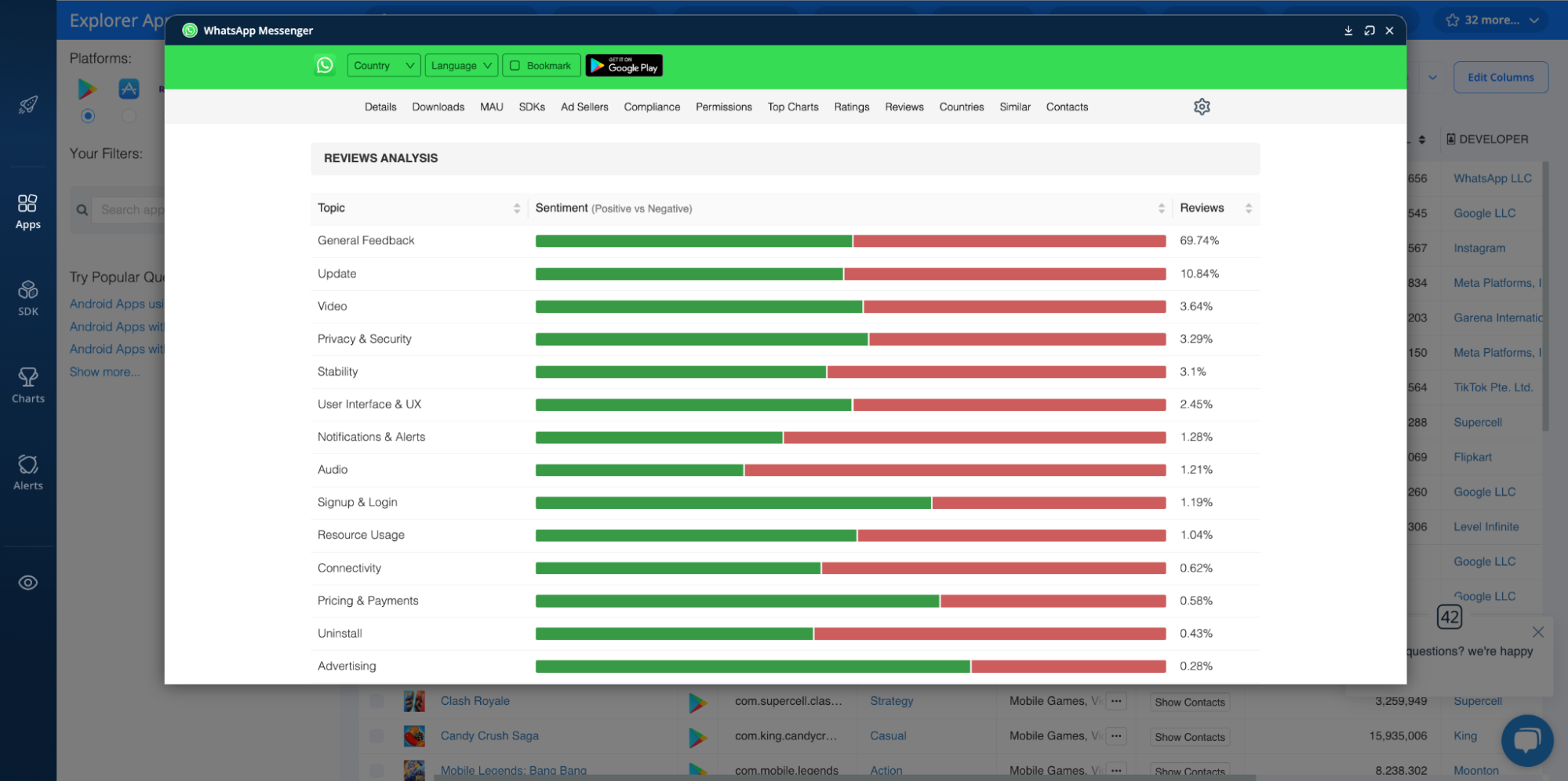
It depicts the percentage of positive reviews versus negative reviews for various topic clusters ranging from ‘General Feedback’ to ‘Privacy & Security.’ You can also use our Reviews APIs to access full text reviews for critical apps.
Publisher and Publisher Website
You can also catch PUAs by investigating app publishers. Do they have a good reputation? Have they published any other apps? Etc.
Likewise, assessing the quality and accessibility of their website and social media presence can be especially enlightening. For example, if the publisher hasn’t put much effort into maintaining their website, or if they lack a certain “personal touch” (e.g. team pages, about pages, etc), you may want to avoid downloading their apps. In other words, if you feel like they’re hiding something, don’t whitelist their apps.
To access publisher details and review publisher websites using the Explorer, see here:
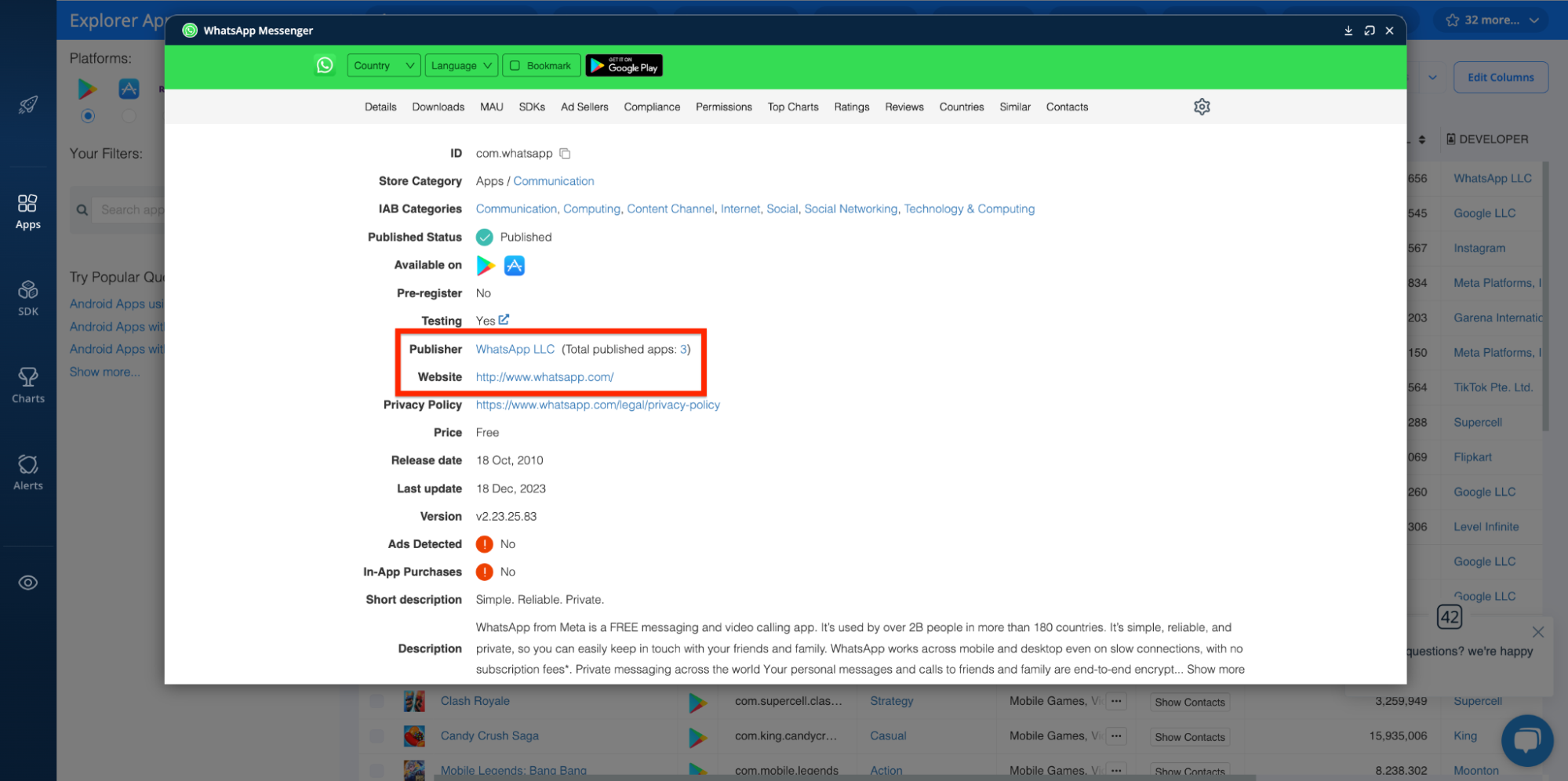
Required Capabilities
In order to make sure users only download apps their devices are capable of supporting, the Apple App Store has a Required Device Capabilities property to determine the hardware and specific capabilities an app requires.
So, similar to sensitive permissions, if an app requires capabilities that don't align with its purported use, that should raise a red flag. This may include capabilities like GPS, location services, microphone, etc.
The 42matters Explorer includes a Required Capabilities filter, so you can find all iOS apps that have access to specific device functionalities:
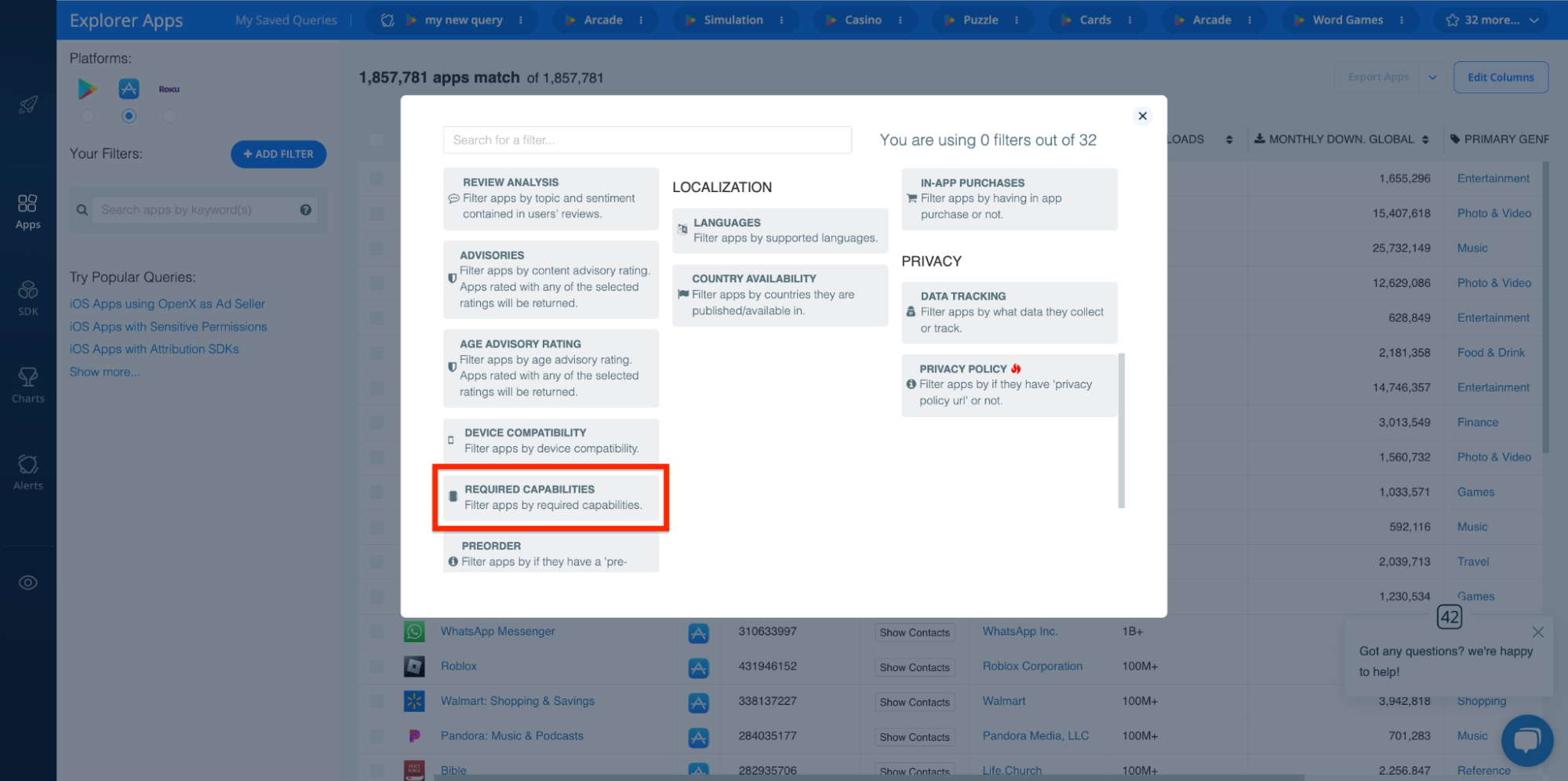
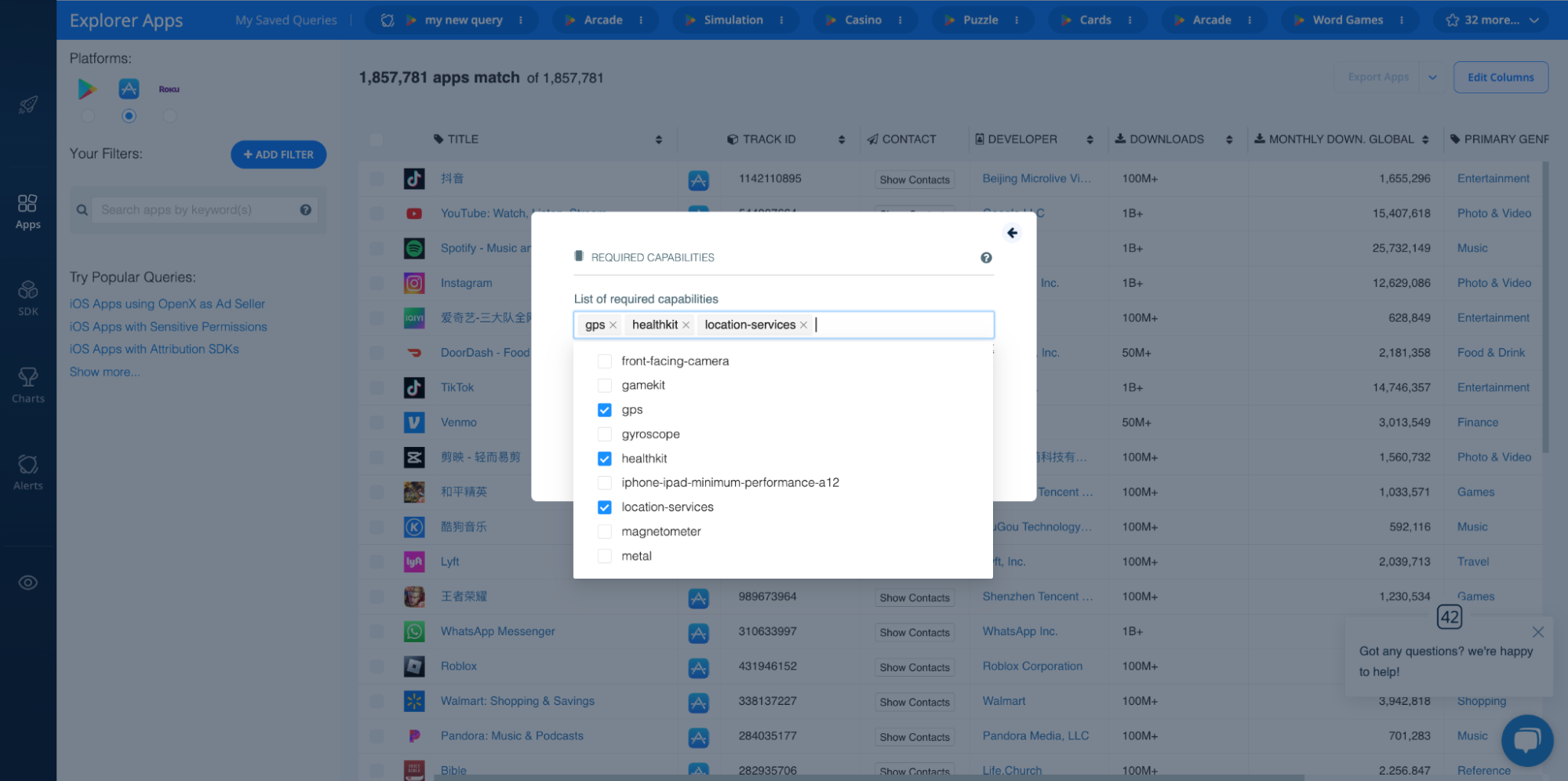
You can also do this in reverse. To see which device capabilities are required for specific apps, open their app profiles in the Explorer and scroll to the Required capabilities section above the Changelog section:
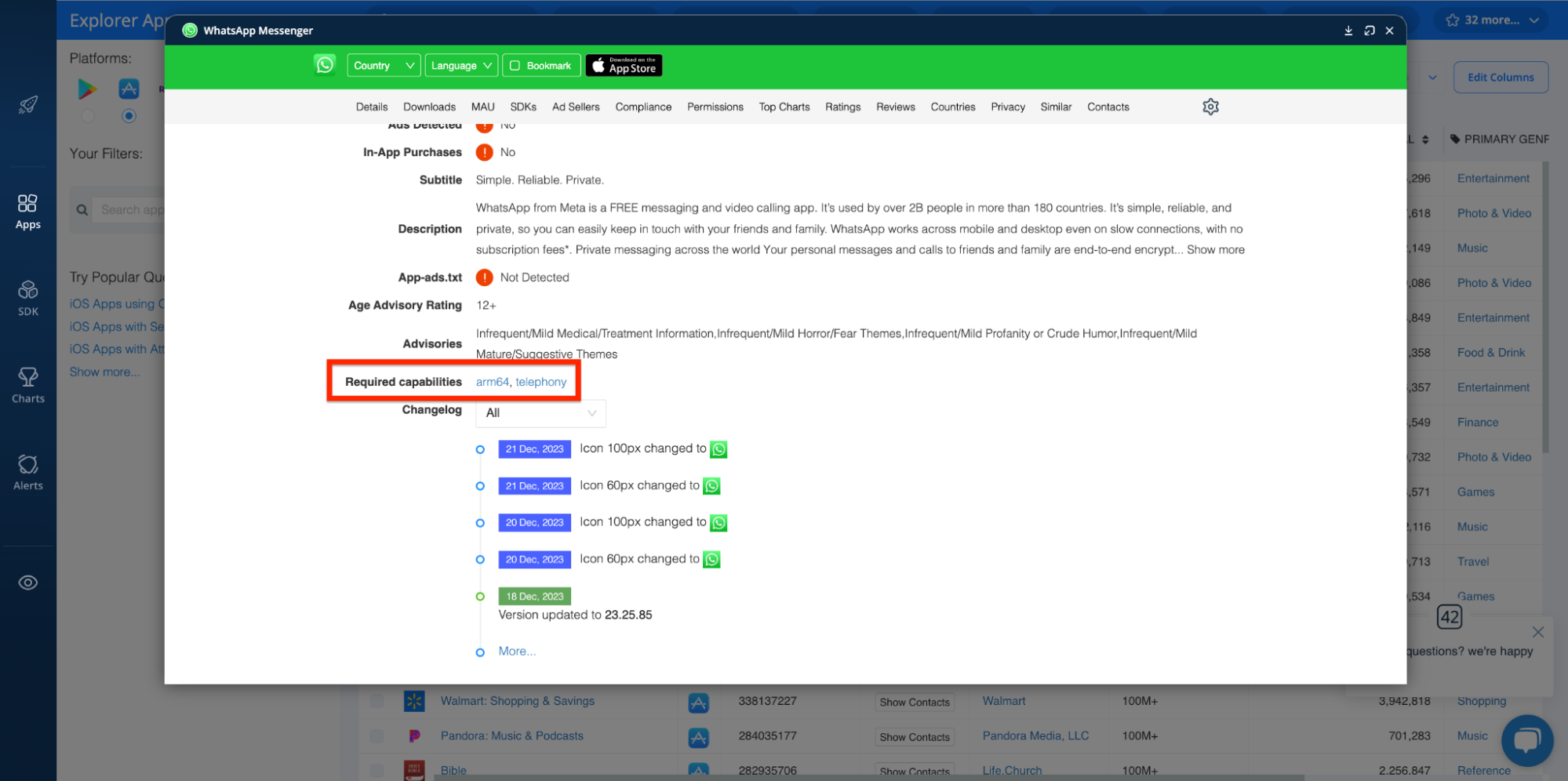
Update Frequency and Abandoned Apps
Apps that are rarely or never updated may be abandoned or less secure, potentially becoming targets for malicious use or otherwise indicating that the app was developed for illegitimate purposes.
You can use the 42matters Explorer to audit an app’s release date, most recent update, and current version:
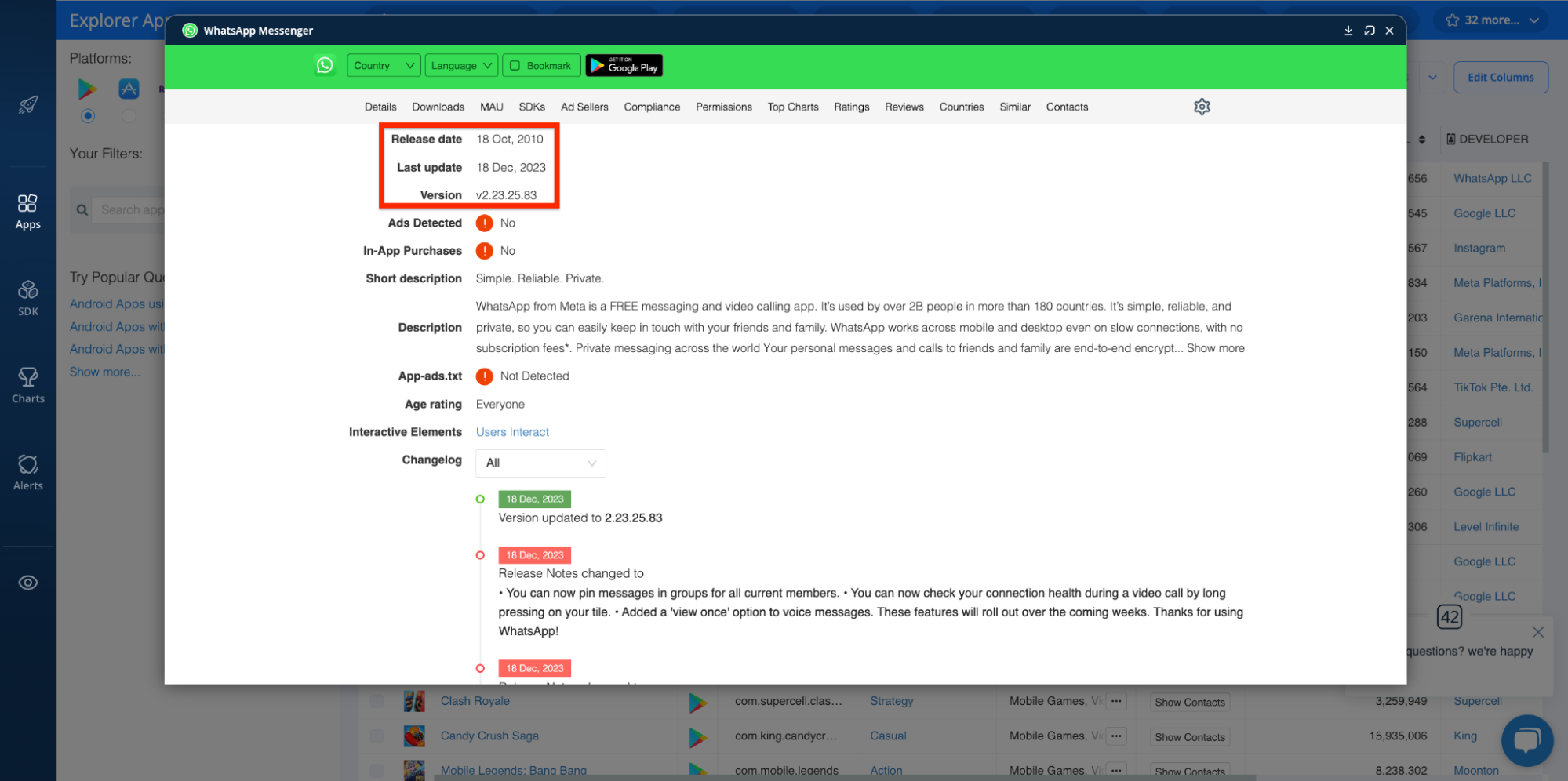
In addition, you can use it to peruse changelogs, release notes, and developer updates:
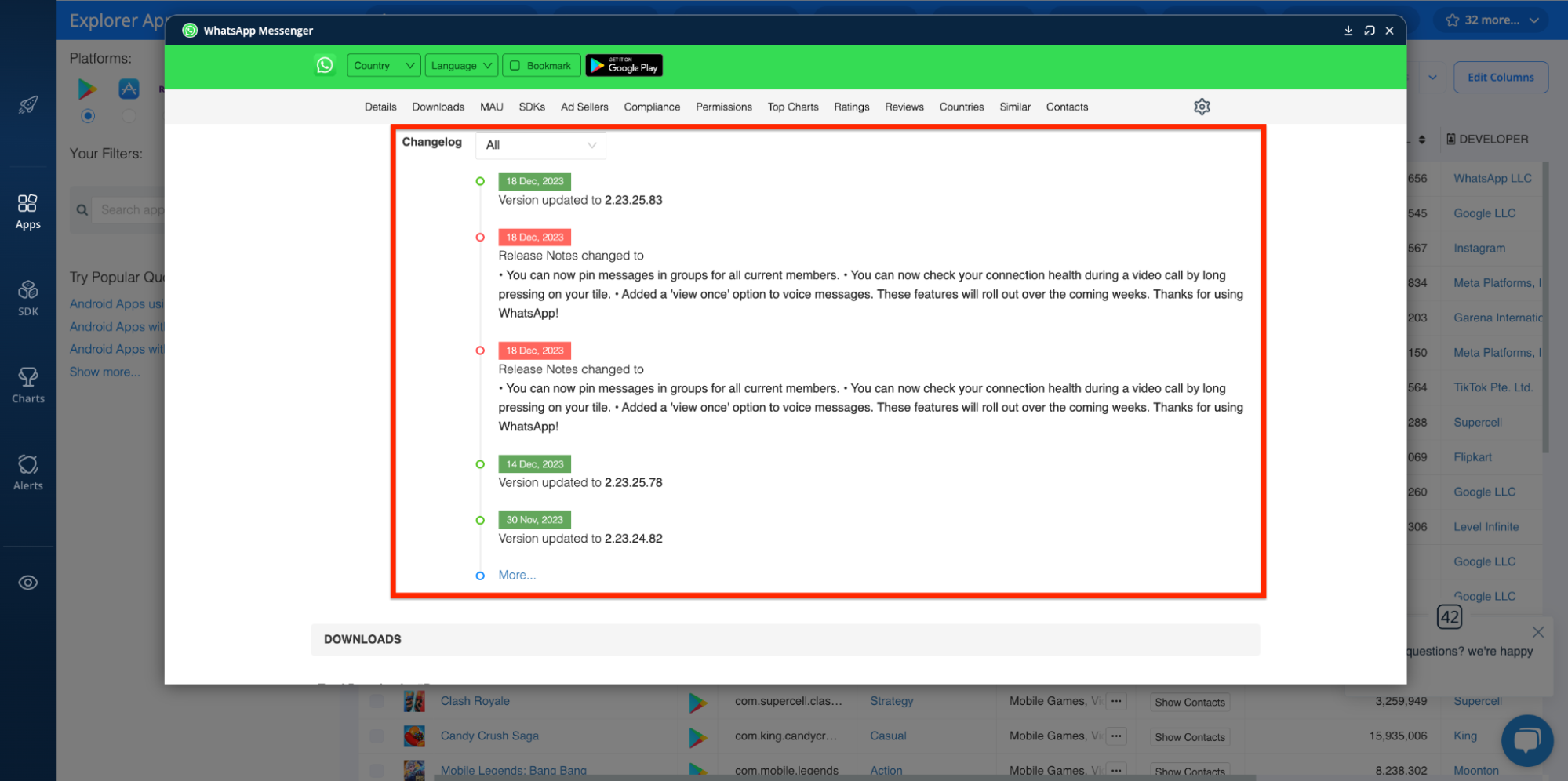
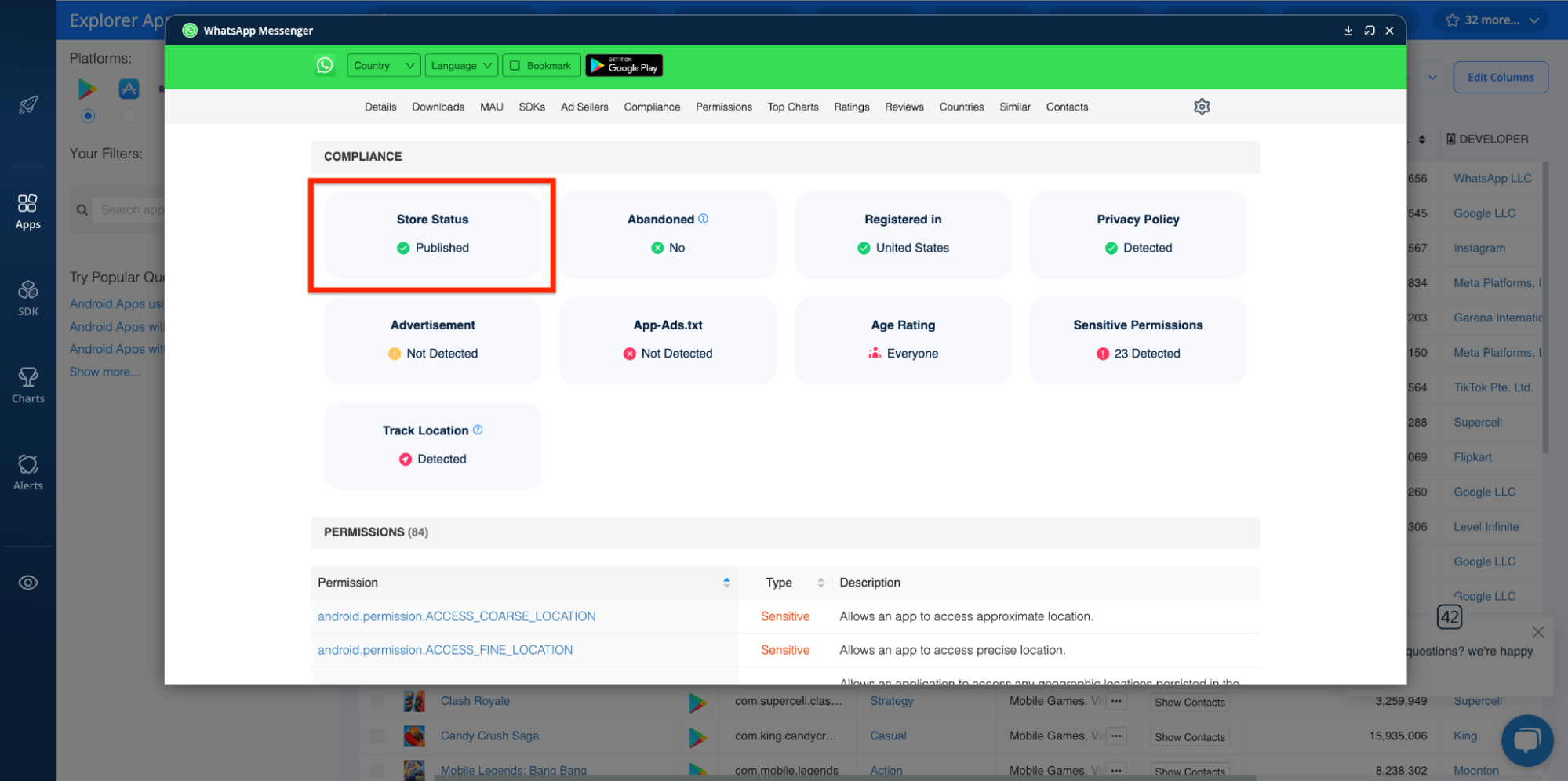
Publication Status
Along the same lines, if an app has been removed from Google Play or the Apple App Store, or if it has a history of being taken down and republished, it warrants further investigation.
With the Explorer’s COMPLIANCE dashboard, you can monitor an app’s publication status:
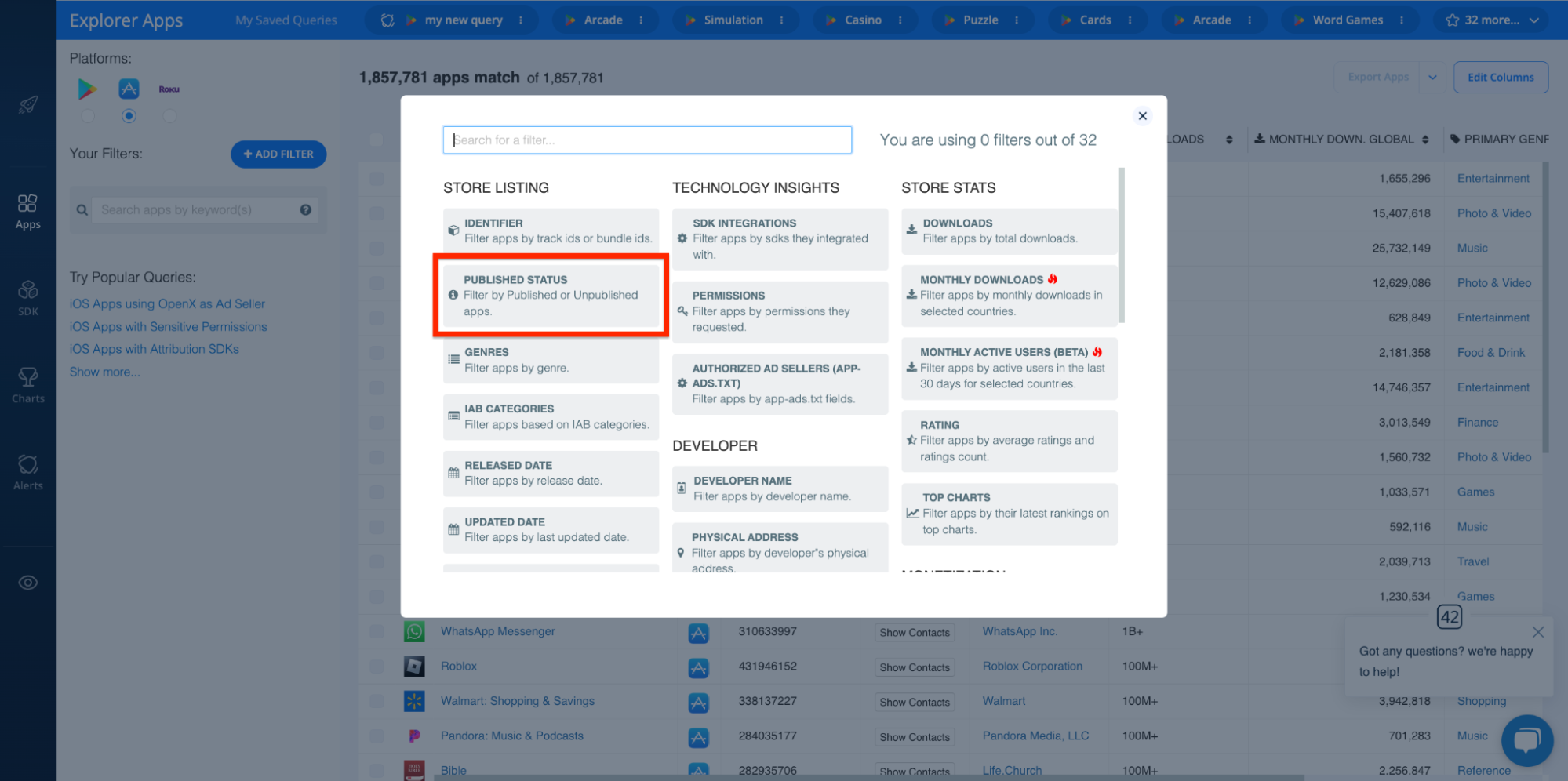
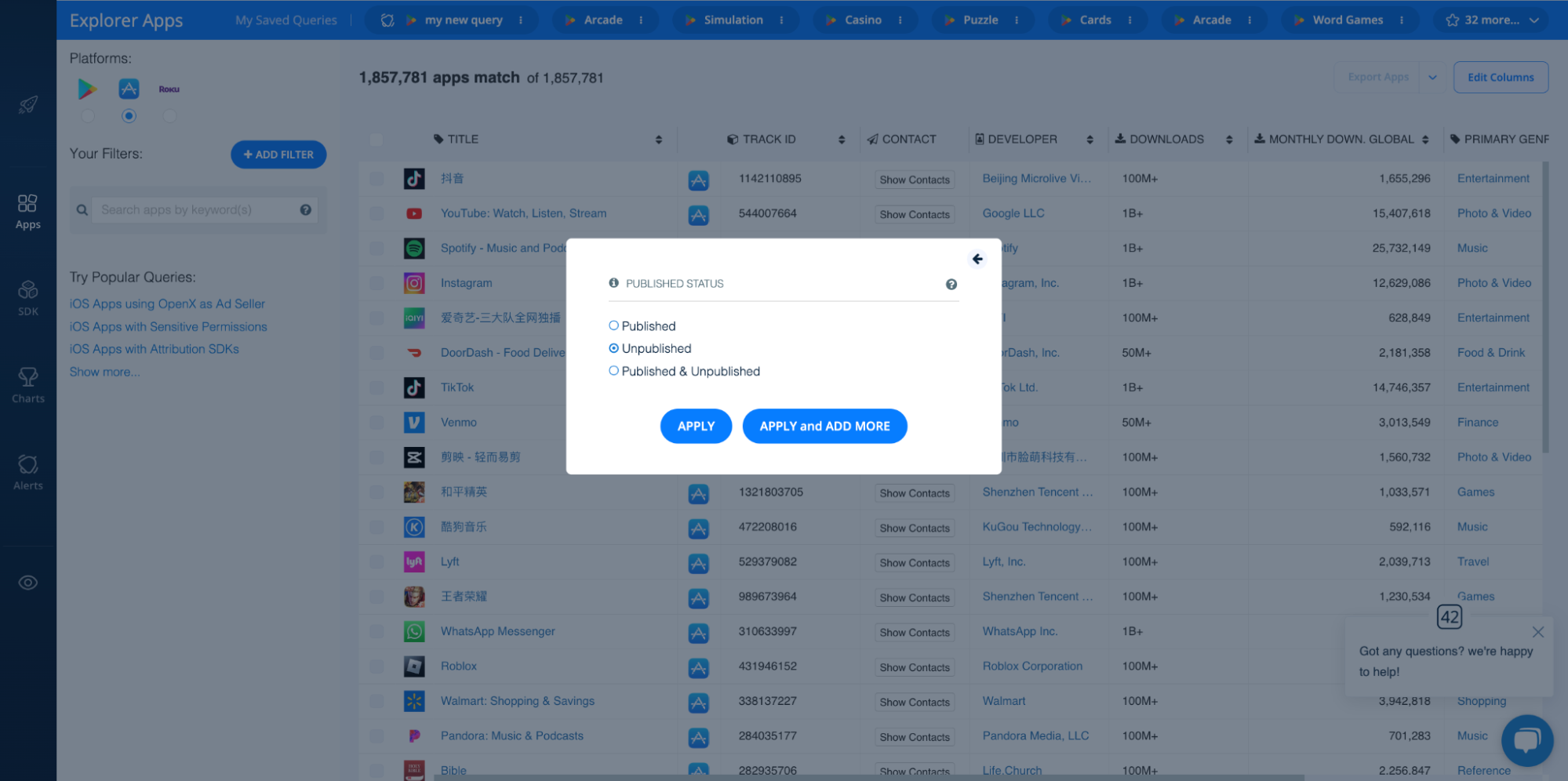
Likewise, you can apply the PUBLISHED STATUS filter to home in on apps that have been removed from app stores. Like so:
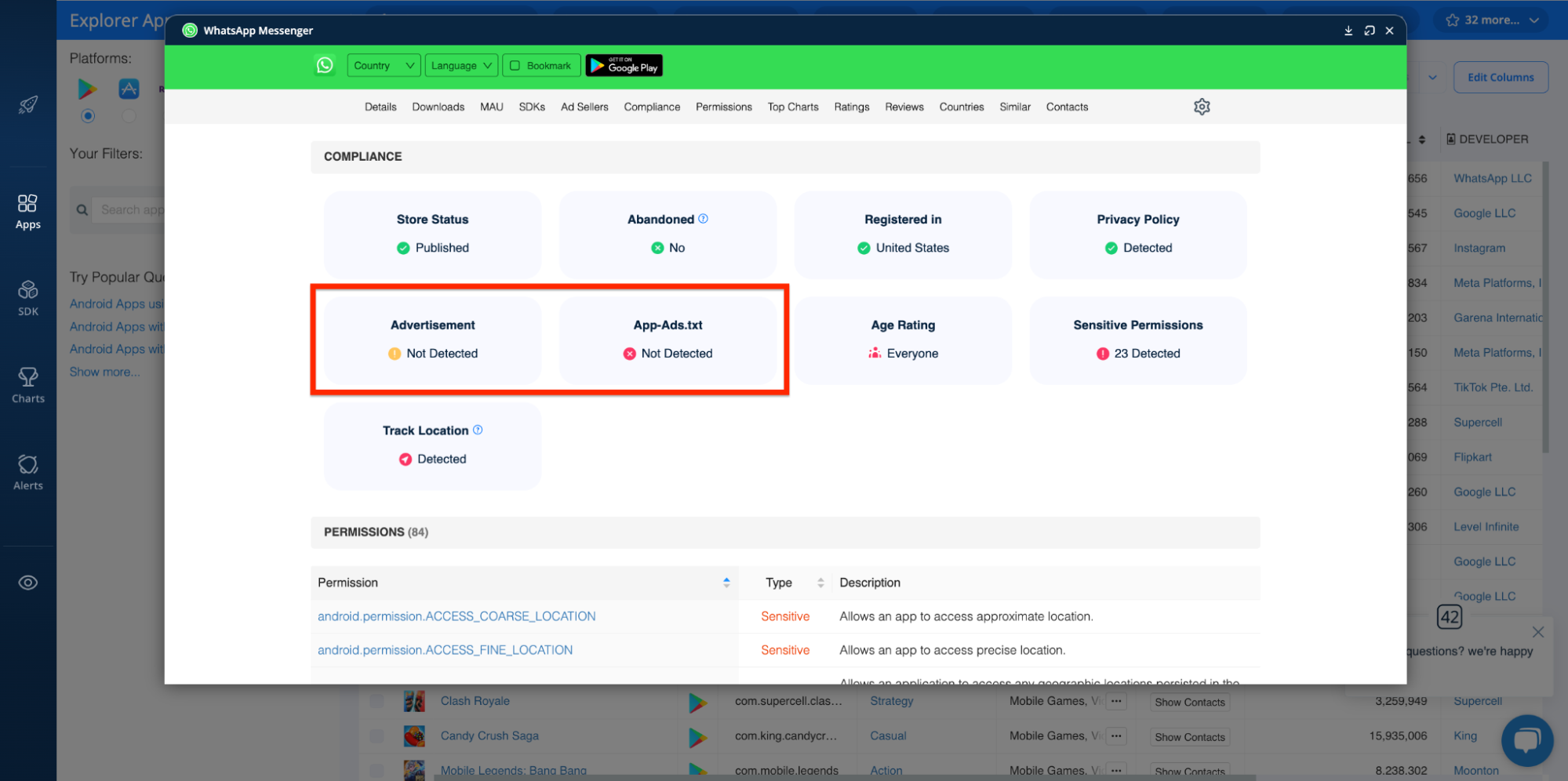
Advertisements and app-ads.txt
As noted previously, not all PUAs/PUPs are “unwanted” for being malicious, some are just annoying. One of the most common sources of annoyance are ads. By reviewing whether app publishers maintain app-ads.txt files, which they may use to combat mobile ad fraud, you can easily omit all ad-supported apps.
Once again, you can use the Explorer’s COMPLIANCE dashboard for this:
Or the Explorer’s AUTHORIZED AD SELLERS (APP-ADS.TXT) filter:
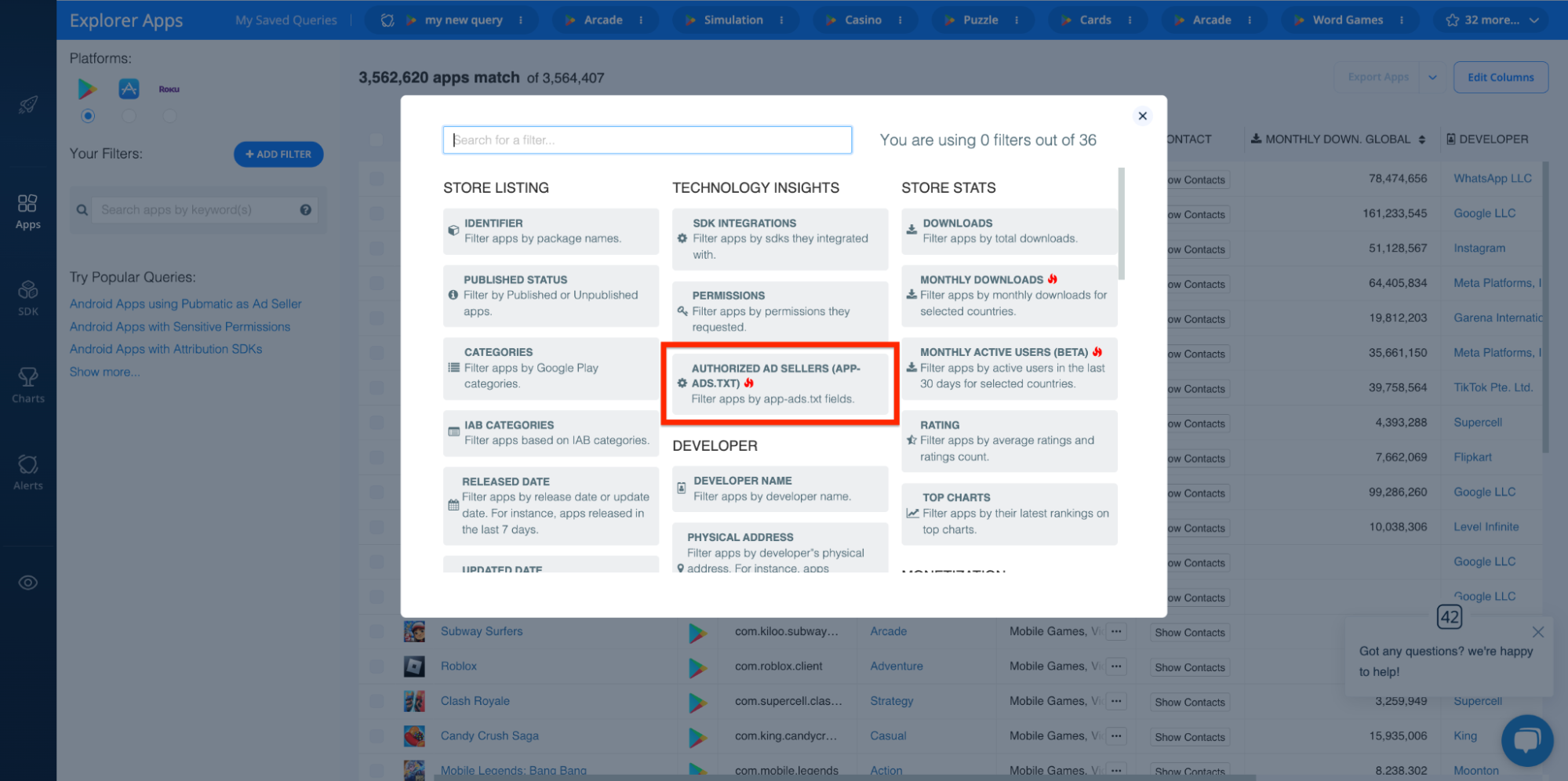
Integrated SDKs
One of the best ways to spot PUAs/PUPs is by taking inventory of app tech stacks and examining the various Software Development Kits (SDKs) they use.
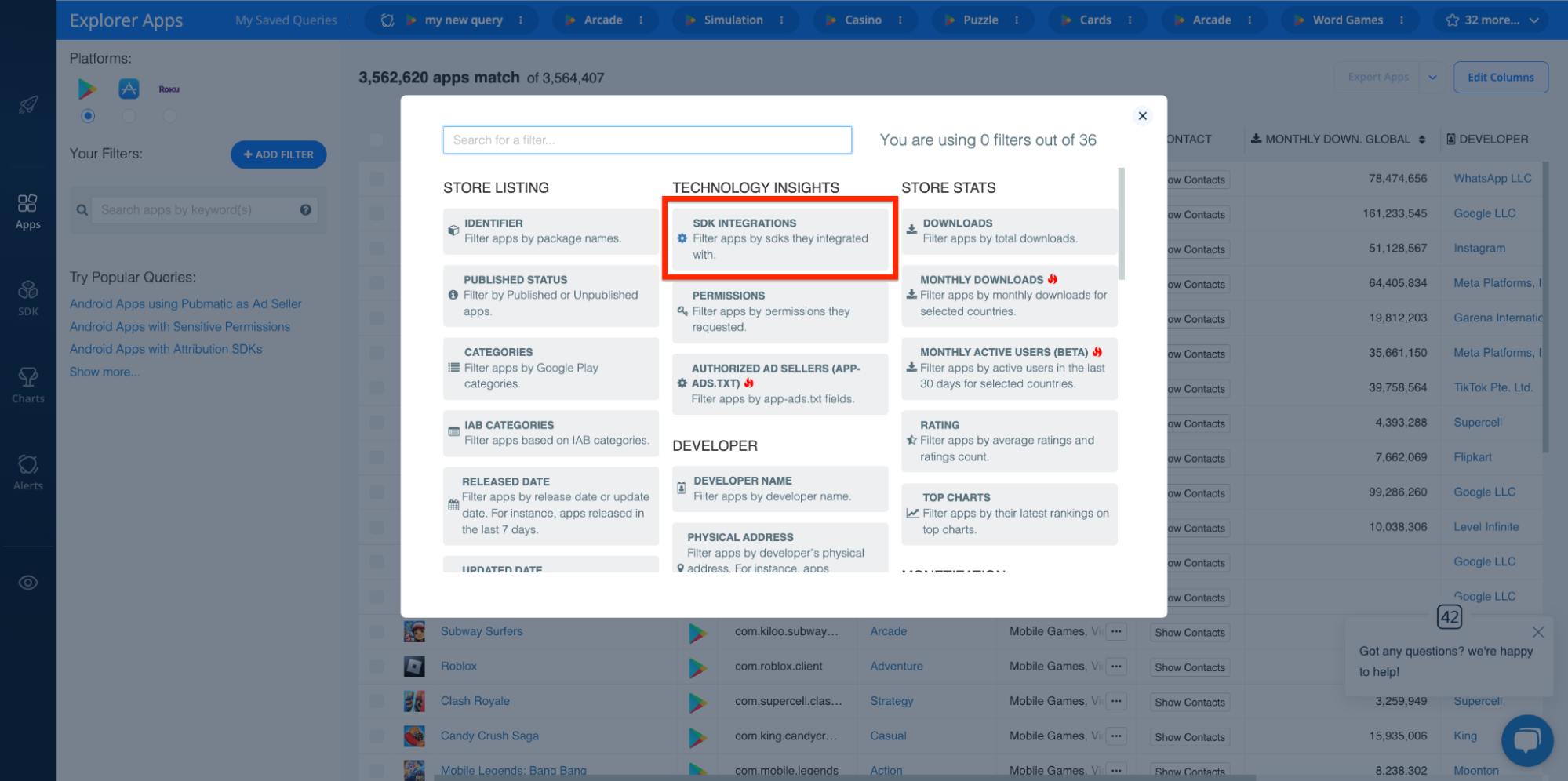
For instance, if you know that a particular SDK has a reputation for scamming end users, you can use the Explorer’s SDK INTEGRATIONS filter to look for all apps that use that SDK and add them to your blacklist. Like so:
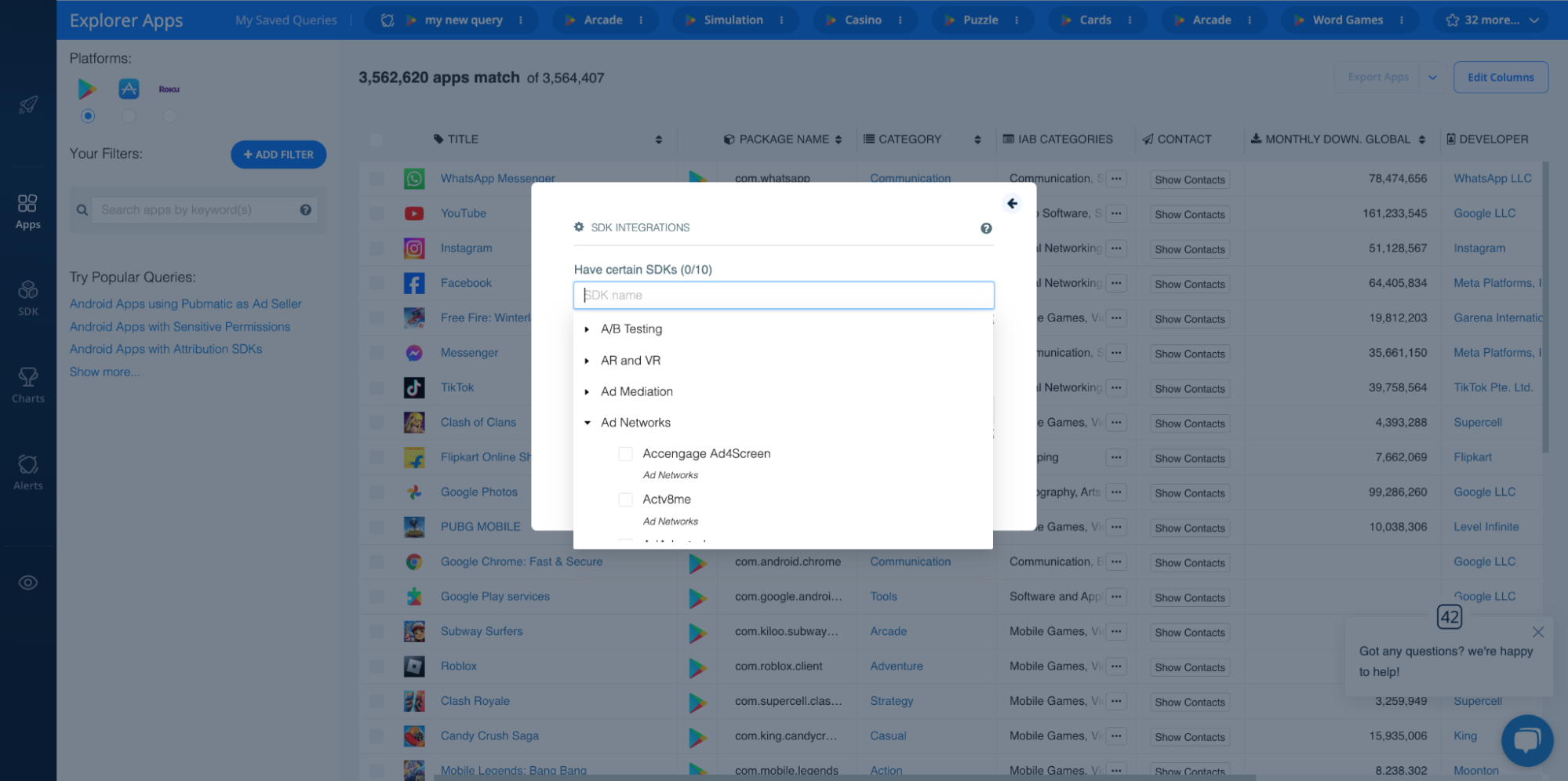
However, you don’t even need to be that precise. Certain types of SDKs are known for tracking user data or for delivering ads. If you notice any apps have SDKs for these purposes, you can investigate them further.
In addition, you can audit SDKs in the following ways:
- Validate SDKs using their SDK IDs: Catch apps that integrate copycat SDKs.
- SDK Developer Website: As with app publisher websites, you can assess the trustworthiness of an SDK by visiting their website.
- Installation and Removal Trends: Patterns in how often an SDK is installed on apps and removed from apps can indicate dissatisfaction or discovery of unwanted behaviors.
To get started with SDK validation and SDK analysis, check out the 42matters SDK Explorer!
Registration Country
Some countries may have laxer regulations on software, leading to a higher likelihood of PUPs/PUAs originating from these regions.
The Explorer’s COMPLIANCE dashboard shows you where apps are registered:
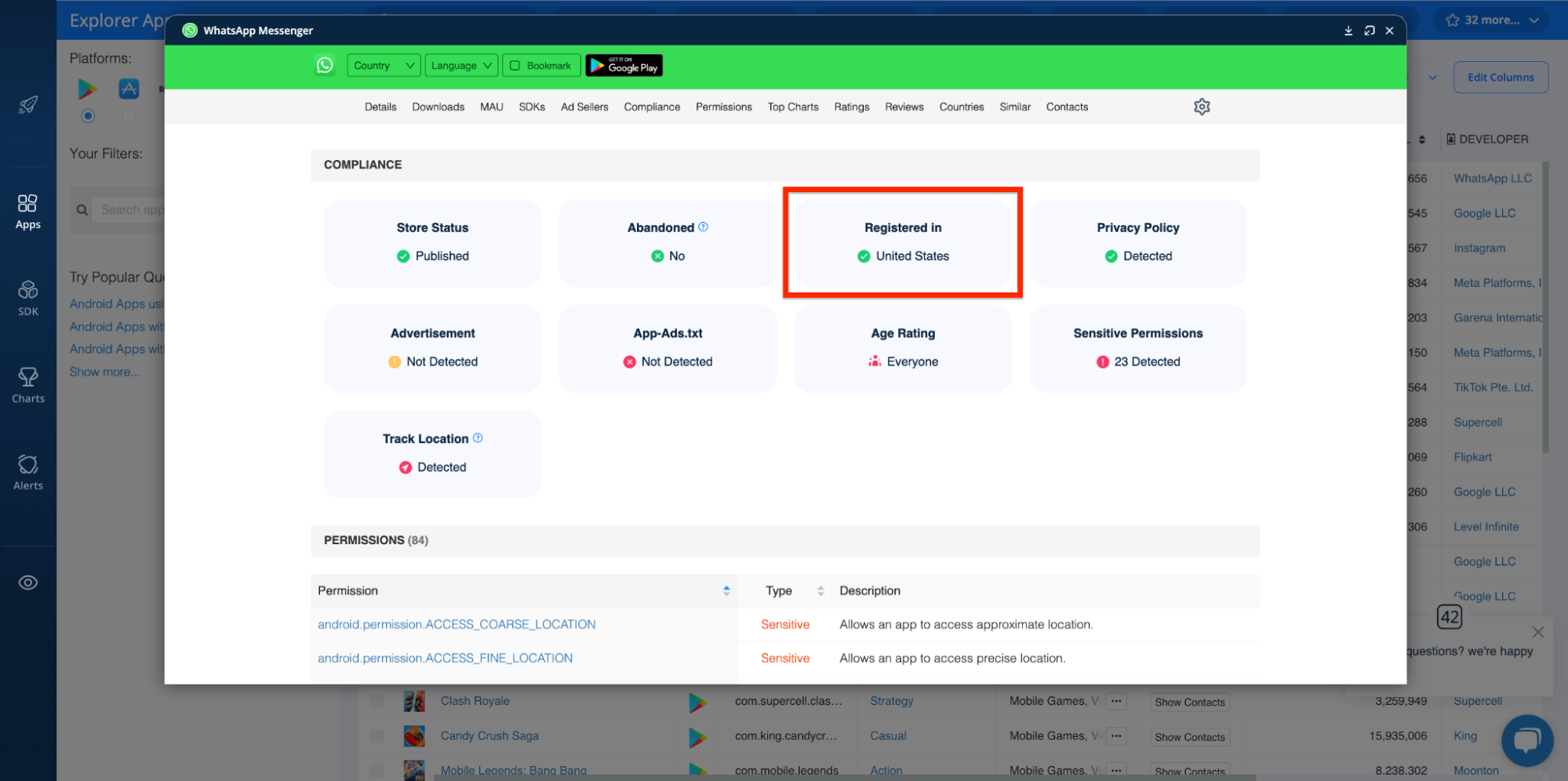
Age Rating and Parental Advisories
Content rating practices like Age Ratings and Parental Advisories indicate the suitability of app content for certain audiences. So, if your use case centers around identifying apps that are unwanted for content sensitivity reasons, these metrics are an extremely convenient way to filter out apps that serve up undesirable content.
Again, the Explorer has filters for these insights:
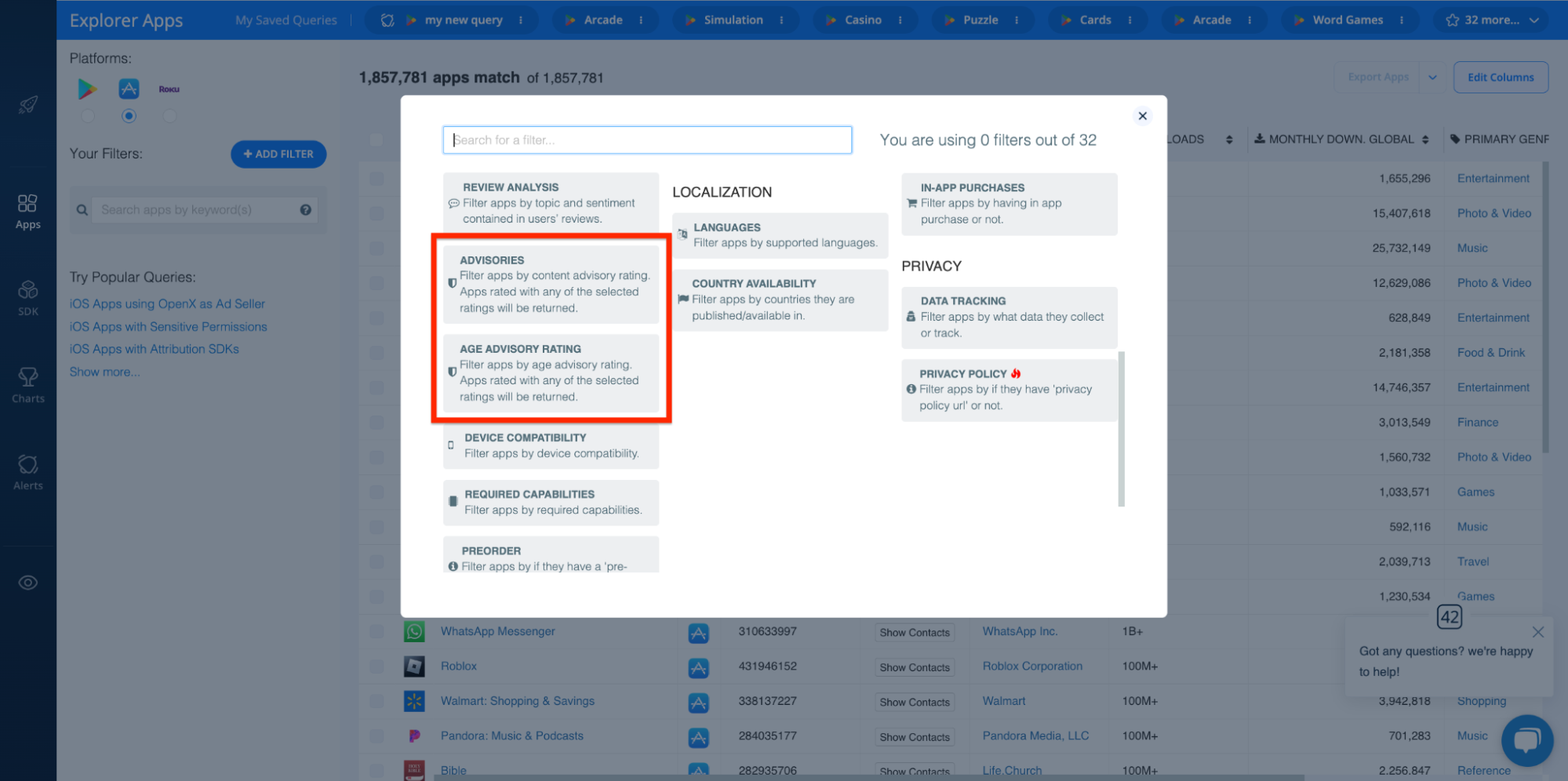
These enable you to find apps that may not be suitable for specific age groups or apps that contain specific types of content (i.e. nudity, gambling, alcohol, etc.).
These insights are also available on app profiles:
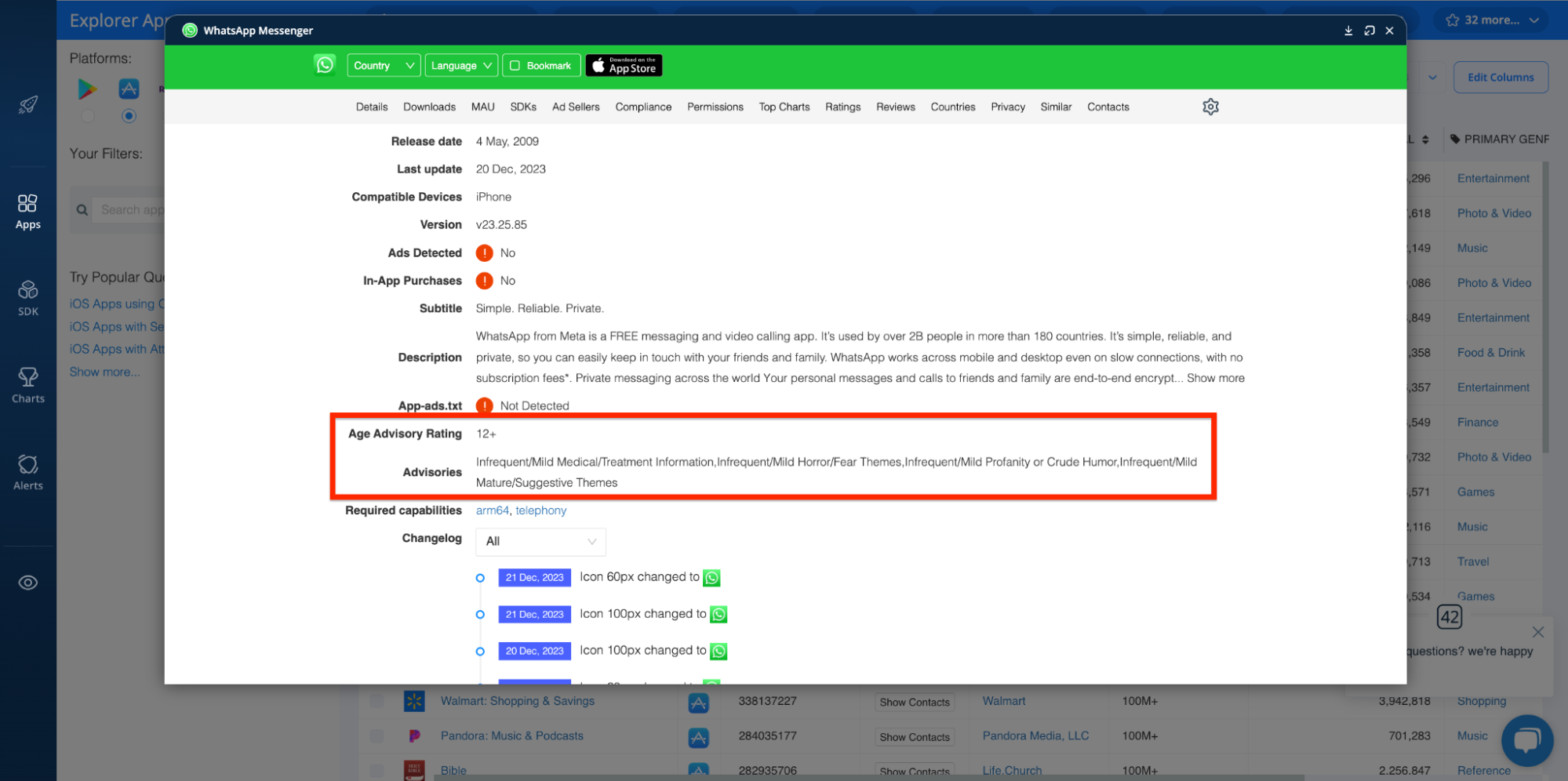
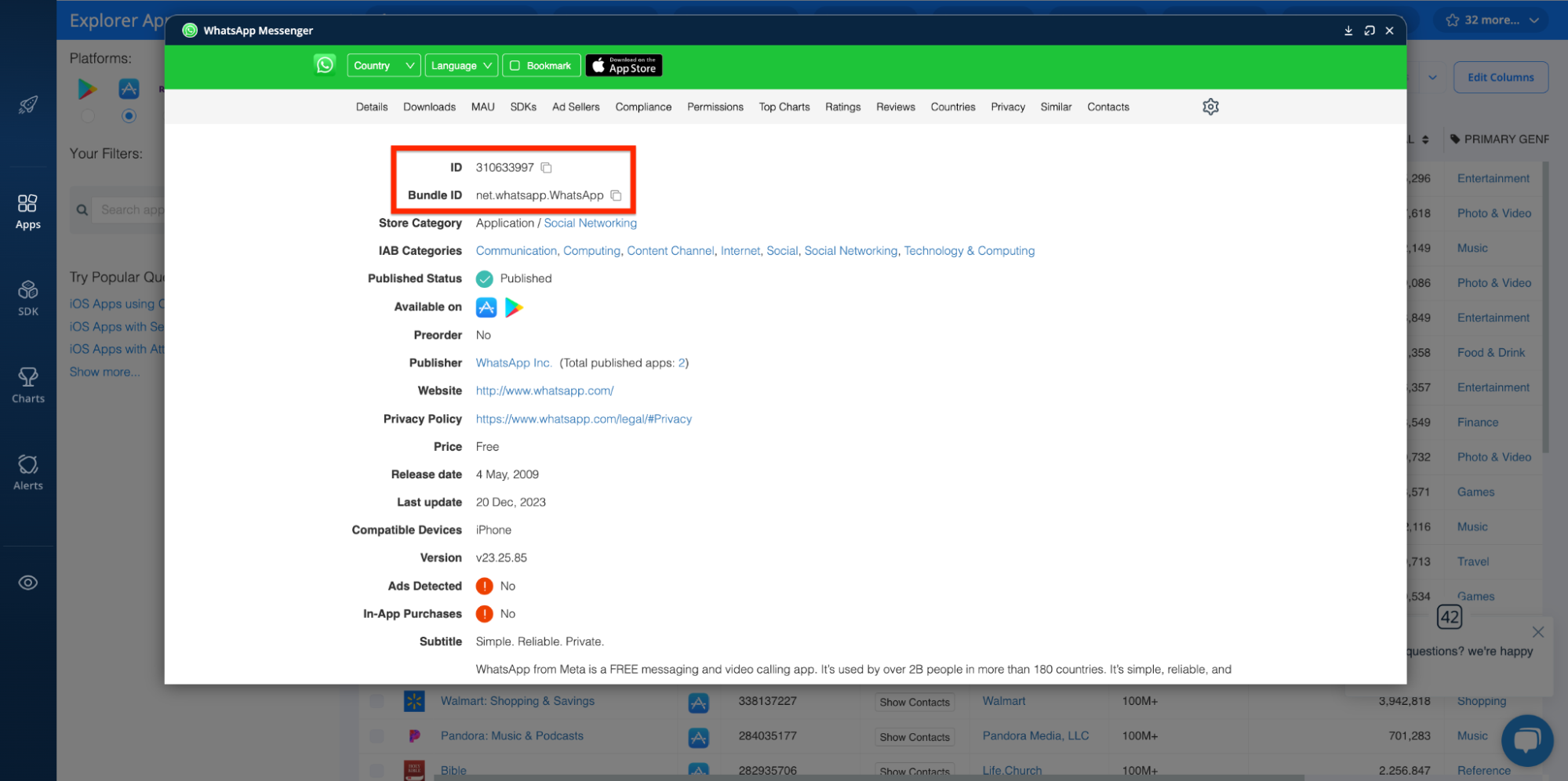
App ID, ID, and Bundle ID
Unique identifiers can help track an app's history and versions, revealing patterns indicative of unwanted software. Likewise, they’re handy when it comes to catching copycat apps designed to scam users.
You can find app IDs in the Explorer here:
Downloads, Monthly Active Users, Other Performance Metrics
Finally, app performance metrics (i.e. downloads, monthly active users, etc.) are generally a good proxy for determining legitimacy. For example, if an app has extremely low uptake and usage, despite being around for quite some time, it’s possible that it’s engaging in manipulative practices, providing little value, or is otherwise offering poor user experiences.
The Explorer provides filters for both downloads and MAUs, which enable you to filter out apps that fall below a certain threshold:
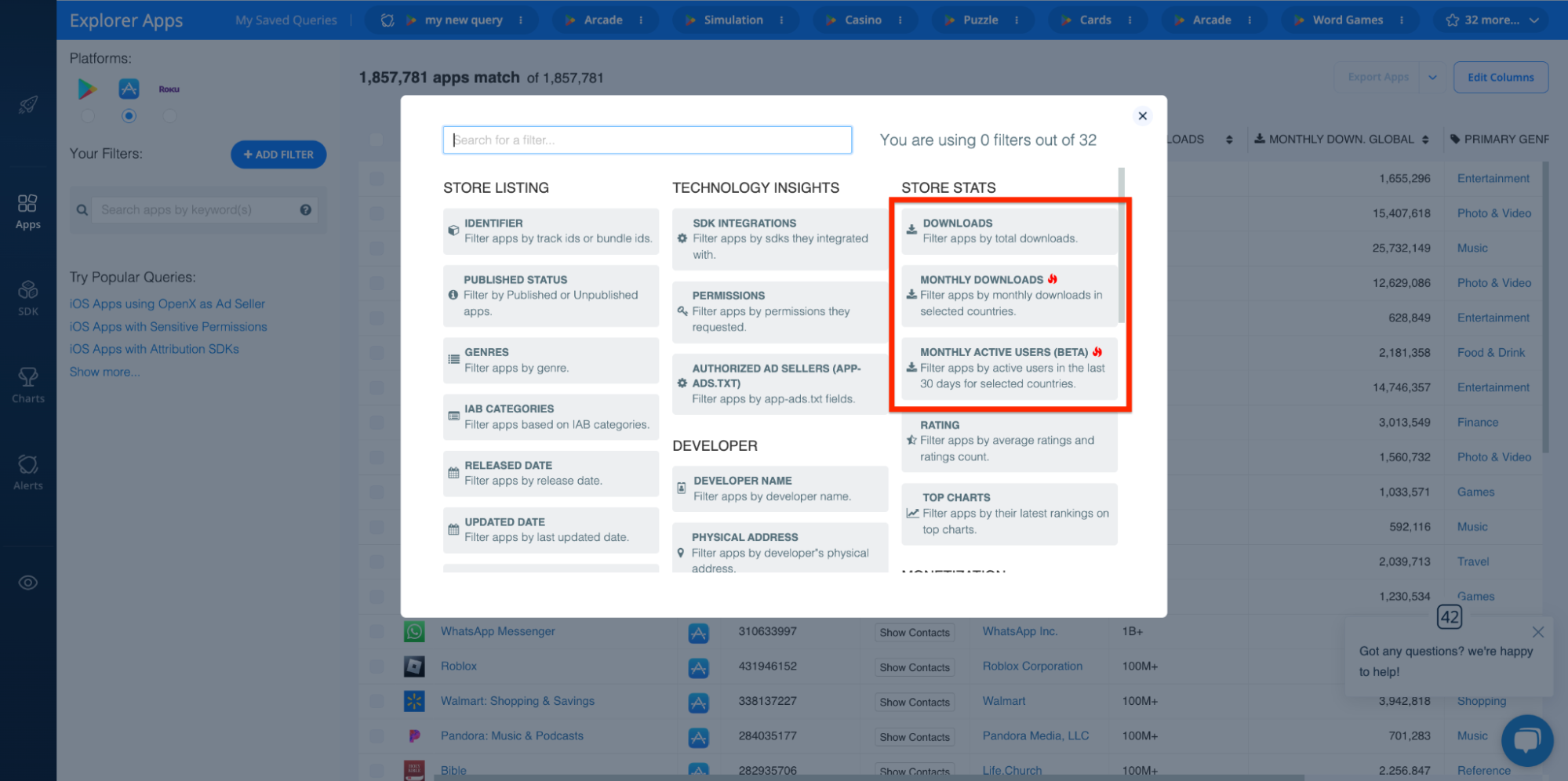
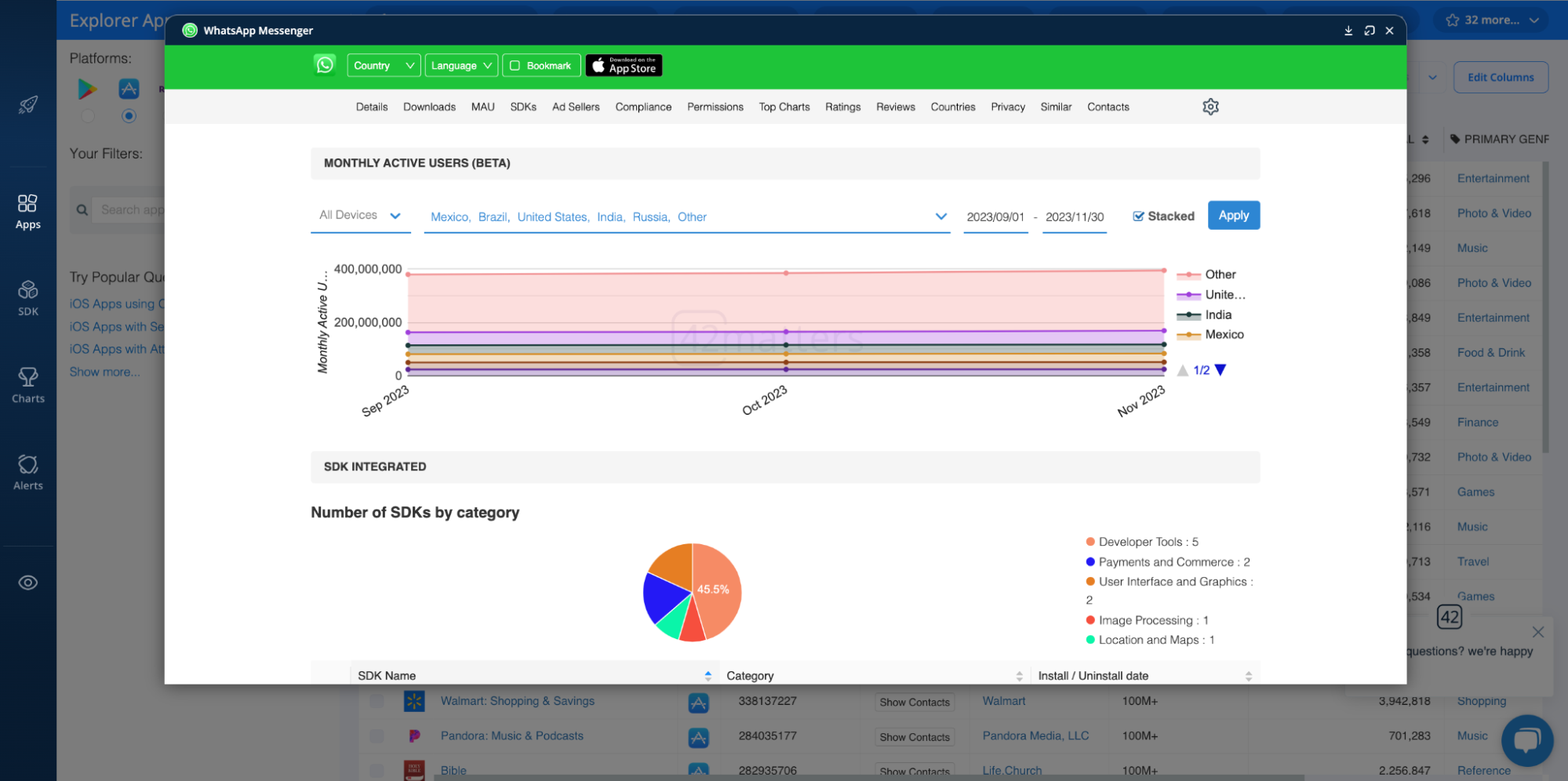
Likewise, you can do a deep dive on particular apps with the downloads and MAU dashboards in each app profile:

API Tools for Detecting Potentially Unwanted Applications (PUA) and Potentially Unwanted Programs (PUP)
To conclude, we’d like to mention our suite of APIs and File Dumps one last time. While the Explorer is a visual dashboard designed for research, our APIs and File Dumps are a little more technical. They provide programmatic access to raw app and SDK insights. This includes all the key data points discussed above that are necessary for detecting PUAs and PUPs.
To see the full list of APIs and File Dumps, and to construct your own strategy for detecting risky apps and SDKs, check out our documentation!
Want to learn more about using our suite of APIs and File Dumps for detecting PUAs and PUPs? Chat with our team!